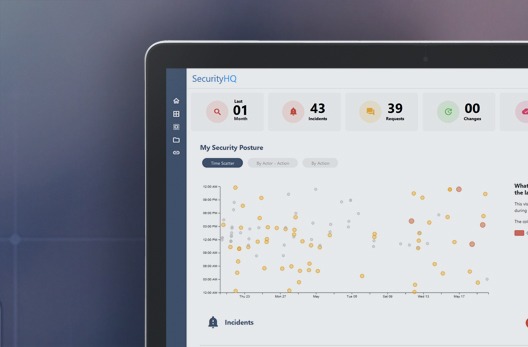
By using Machine Learning algorithms, we categorise patterns of user behaviour, to understand what constitutes normal behaviour, and to detect abnormal activity. If an unusual action is made on a device on a given network, such as an employee login late at night, inconsistent remote access, or an unusually high number of downloads, the action and user is given a risk score based on their activity, patterns and time.
Benefits
Detect Compromised Accounts that have been spoofed, or unwittingly/knowingly had malware installed.
Risk Scoring provides a holistic overview.
View Access and Activity on protected data. See when data was accessed, why, when and how.
Machine Learning Learns by Itself, based on patters of user behaviour.
Less Time-Consuming and More Cost-Effective than delivering and monitoring systems in-house.
Download the Datasheet
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.