MSSP Advancements • 10 Min READ
How MDR is Used to Spot Third Party Risks, Insider Threats and More.
by Eleanor Barlow • Oct 2020
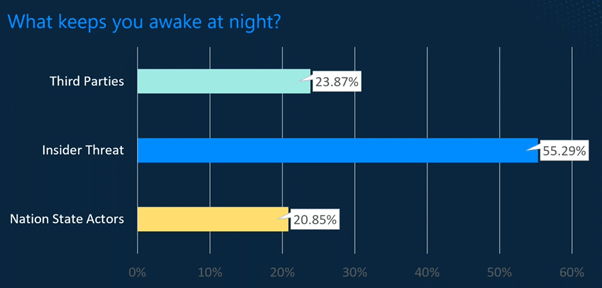
In a recent survey, SecurityHQ asked over 70,604 cyber security professionals the question, ‘What Keeps You Awake at Night? Third Parties, Insider Threats, or Nation State Actors?‘. The results showed that, out of the three options, over 55.29% of those who took part said that Insider Threats concerned them the most. Followed by Third Party Risks, at 23.87%. And, finally, Nation State Actors at 20.85%.
What we aim to identify in this blog, is how Managed Detection and Response (MDR) can be used to defend against such threats and reduce the attack surface of an organisation.
Table of contents
Managed Detection and Response (MDR) in a Nutshell.
MDR is a Managed Security Provider (MSP) service that provides companies with the people, processes and technology to hunt out and respond to threats, so that dangers are made visible and the attack surface is reduced.
MDR supports organisations by providing round-the-clock monitoring to detect, investigate, notify & respond to incidents. Powered by real-time log analytics, with security orchestration automation & response tooling, MDR provides true visibility, and rapidly identifies & limits the impact of security threats for organisations, so that processes are optimised, and business can run undisturbed by cyber-attacks.
The Core Benefits to Businesses Using MDR Services
- 24/7 Detection of threats powered by real-time analytics.
- 24/7 Incident response supported by GCIH certified incident handlers.
- Advanced Correlation & ML to detect complex threats.
- Incident Containment & Triage Contain threats via incident playbooks & SOAR platform.
- Automate containment response to block threats.
- Reduced Cost & Complexity & up/ downscale effortlessly.
- Improved Speed of detection & response.
- SLA provides detection, analysis & notification within 15 minutes for critical events.
- Security Analysts available on demand.
- Measures tailored to the specific needs of the company.
What are the MDR Steps Used to Safeguard Against Threats?
01: Data Collection
(Syslog, Cloud API, Agentless Windows, Apps & Databases).
Essentially, accurate and rapid MDR depends on the initial data collection. There are many systems out there, buzzing away, both on-premise and on the Cloud. You need to be able to get the data from those systems, process it, correlate, and analyse those systems. Whether via traditional Syslog, Cloud API, AWS, Azure, Statistical Analysis Systems (SAS) services, or something else, you need to get that data, and have it presented in a way that can be processed quickly and efficiently.
And, once you have the right logs, they need to be validated.
02: Data Processing
(QRadar SIEM Analysis and Correlation, Identify Risky User Behaviour, Contextualise Intelligence).
Once you have the logs, you can start to standardise and normalise them. Start with basic correlation. By contextualising the traffic logs against threat intelligence data, analysts can see where risky user activity might be present. This, very quickly, moves along to advanced analytics. Which is where it begins to get a little more interesting.
03: Advanced Analytics
(User Behaviour Analytics (UBA), Business Service Risk Profiling, Anomaly & Behaviour Algorithms).
Business Profiling, otherwise known as Corporate Profiling, is the process that provides a map of an organisations structure, its people, processes, technology, client relationships and third-party interactions.
Now, if you take this and profile the crown jewels of a given business, take highly sensitive critical system data for instance. If you can profile that, understand what the normal user connections are, who are the admins, what are the processes, what are the executions, and then rank the anomalies against them, it makes it easier to spot anomalous or malicious activity.
That sounds relatively simple, but this can be quite challenging because first you need to classify your systems. This does not include the classification of malware, or security controls monitoring. Why? Because if there is an inside threat, then this threat is, potentially, a legitimate user. Which means that they are not going to trigger as a malware alert. They are not going to trigger any sort of tripwires or honeypots that you present. So, to spot them, you need to look for anomalies in the way that data is accessed, and the service is profiled.
User Behaviour Analytics (UBA) forms a supplementary layer to security, to provide complete visibility, detect account compromises, and mitigate and detect malicious or anomalous insider activity. By using ML algorithms, patterns of user behaviour are categorised, to understand what constitutes normal behaviour, and to detect abnormal activity. If an unusual action is made on a device on a given network, such as an employee login late at night, inconsistent remote access, or an unusually high number of downloads, the action and user is given a risk score based on their activity, patterns and time.
Follow the Money
When you are doing business profiling, you have to follow the money. This means deciphering what area, if compromised, is going to destroy your business. It could be a Customer Relationship Management (CRM) system, your accounting system, or your sales system. It’s about knowing, within your specific business environment, what area is most vulnerable. Say, for instance, HR goes down, this may have a low risk score within your company. But if your oil trading platform goes down, that could bring down your entire business. Every company has a different way of doing security. And once you understand the specifics of an organisation, then you must see who the users are on each system. Admin users and privileged users are just as risky as outsider threats, and they need to be monitored.
Now, say the person running the CRM system for your bank, who you saw this morning, dials in from Jamaica. This unusual activity is then given a use case. It is these use cases that set up the triggers of the alarms and triggers the quality alarms.
Once you have this, you know what to really protect. And if there is a hack, you know what to prioritise.
04: Analysis, Detection and Response
(400+ Analysts, 24/7 Detection and Response, Eliminate False Positives).
Being able to detect a threat is useful, but unless you can act on it effectively, it is useless. Speed of response is crucial here, which is why detection and monitoring must be 24/7. This requires an army of analysts.
In fact, to highlight a problem, the root cause of a problem, how to mitigate it, and how to contain it requires skilled experts round the clock. Many organisations can set up an analytics platform but having the skills and team to monitor 24/7 is too costly for most. Which is why MSP MDR is a cost effective and pragmatic measure.
05: Business Intelligence and Reporting
(Data Driven Documents, Rich Analytic Reports).
This whole pipeline is a big data challenge. You could have 5000 logs coming into the system per second. This is a vast amount of information, and you need to be able to visualise it in a way that is highly graphical, to understand everything being analysed.
Regardless of the SIEM tool used, whether it is IBM QRadar, Splunk, or something else, you need to be able to put an overlay on top of those systems to be able to report and visualise what data really means in an intelligible way.
In short, we look for quality alarms over the quantity. You don’t want 400 alarms a day. You want the 15 that you need to action and do something positive with.
06: Incident Management and Analytics Platform
(Incident Management Platform, Orchestrate Incident and Response, Improve Quality and Context for Incident and Response).
Once a threat is detected, it is visualised and reported via an incident response platform, which is used for everything from tracking speed of response to incident management auditing around workflows, and more.
Response is a time-based thing. Which is why technologies, such as IBM threat containment orchestration and response tooling can be used as part of MDR.
07: Threat Containment
(Mitigate Risks, Block Malicious IP’s, Suspend Rogue Users).
The quicker you can get something contained, the safer and better it is for all. Which is why it is necessary to orchestrate and automate a response to block or isolate an infected machine.
Skilled MSP experts are trained to identify attacks and mitigate threats before any impact is made.
08: Log Management and Compliance
(Secure Log Storage, ISO 27001).
Different businesses have different compliance rules.
Banking has a whole regularity system and different compliance requirements that are very different to say security requirements within healthcare. But whatever your compliance requirements are, controlling the users, the logs and the security is crucial to meet compliance requirements, because they are ordered accordingly.
Compliance with ISO/IEC 27001, as part of MDR, is an easy and efficient way to conform with regulations regarding data protection, information security & cyber security. Particularly with concerns to handling financial, personal, and client-sensitive information.
And having the ability to look at some logs from a year ago, with the intelligence that you have today, is not only unbeatable, but necessary.
The first thing to note is that the incident management process should not be focused on firing alerts at customers. Such a system hinders, rather than helps. The important thing is to prioritise and action the most crucial elements first. No security company wants to be an ambulance service.
Whereas if you identify risks, and see where there is a rogue connection that needs to be hardened on say, a firewall, or if there is a large number of authentication failures that should not be there, then you can present these issues, via visualisations, back to the business to action.
The key thing here is to operationalise security and prioritise tasks. The ability to detect the one hundred tasks in front of you, and then be able to categorise these tasks so you know which three are your top priority for the day, is what the MDR service provides.
Regardless of how good your internal team may be, the experts within security operation centres are the ones with their eyes on the glass, who can rank issues, order and separate the major events from the minor concerns. By dealing with issues that are a high priority first, you deal with the challenges that have the biggest impact on closing out security loopholes and protecting your organisation.











