Notes from the Field • 6 Min READ
What Keeps You Awake at Night? Third Parties, Insider Threats, or Nation State Actors? Survey Results Explored.
by Eleanor Barlow • Jun 2024
[The content of this blog was original created September 2020, and was updated June 2024]
SecurityHQ released a poll within the cyber intelligence group, ‘Advanced Persistent Threats (APT) & Cyber Security Threat Actor Group’ which contains over 70,604 cyber security professionals. Here the question, ‘What Keeps You Awake at Night?’ was posed.
The Results
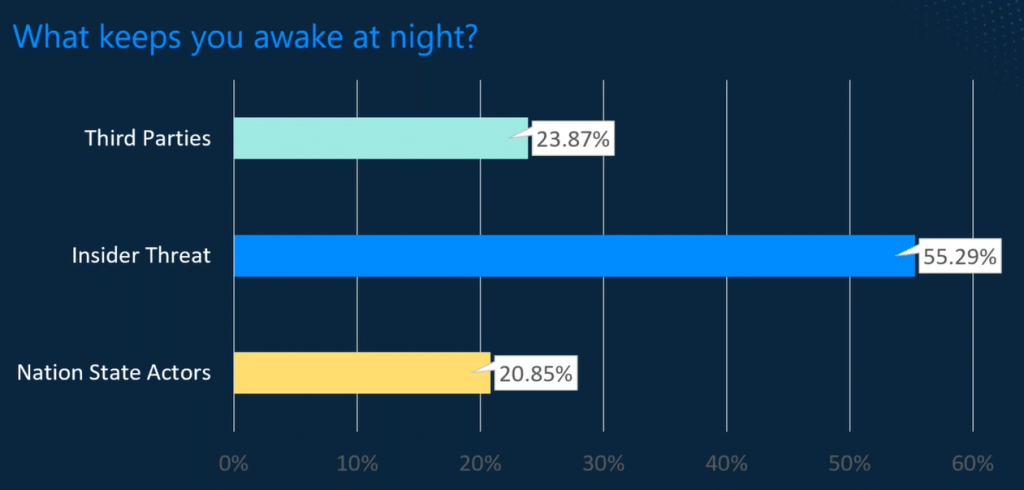
Over 55.29% of those who took part in the poll said that Insider Threats kept them awake at night. Followed by Third Party Risks, at 23.87%. And finally, Nation State Actors at 20.85%.
What is an Insider Threat?
While some attacks are vindictive, many employees/insiders are completely unaware that they are a threat at all.
Most of the world now works remotely to some level, which increases the likelihood of connecting to an unsecure device. Take an employee working remotely. This employee may be sitting at a local café where they decide to work on a company device. If this device was targeted while using an open Wi-Fi connection, there are a number of ways a malicious actor could penetrate the device and view and/or spread malicious malware throughout the company.
Internal teams pose as much of a threat as external attacks, and both malicious and accidental internal security breaches are regular occurrences. Infact, ‘66% of organizations consider malicious insider attacks or accidental breaches more likely than external attacks.’ (TechJury).
How to Reduce Insider Threats
Security training is essential. Employees must be aware of the company’s security protocols and measures, both in and outside of the office.
They must also be aware of how to keep their data/devices secure, so that potential malicious insider threats are limited.
Everything from what to do in the event of a breach, to how to avoid phishing scams, must be taught.
Second, User Behavior Analytics is essential to understand the actions within an organisation, and to highlight and stop unusual activity before the damage is done. By using ML algorithms, expert analysts can categorize patterns of user behavior, to understand what constitutes normal behavior, and to detect abnormal activity. If an unusual action is made on a device on a given network, such as an employee login late at night, inconsistent remote access, or an unusually high number of downloads, the action and user is given a risk score based on their activity, patterns and time.
And while all three threats presented in this poll have risen over the last couple of years in both scale and sophistication, according to IBM’s ‘The Cost of Insider Threats’ report, ‘Negligent employees or contractors were the root cause of 2,962 of the 4,716 incidents reported.’
Third Party Risks on the Rise
The majority of organizations use third parties, including vendors, partners, e-mail providers, service providers, web hosting, law firms, data management companies, subcontractors and so on. From IT systems to sensitive information shared with legal teams, these third parties could easily be a backdoor into systems for attackers to infiltrate.
Not only are more organizations using third parties, but we are seeing more attacks via third parties to infiltrate multiple networks. Blackbaud, for instance, is a system extensively used by the education sector as well as non-profits, healthcare, and religious organisations. The system was compromised and the attack meant that ‘at least 10 universities in the UK, US and Canada had data stolen about students and/or alumni after hackers attacked’. This is an example of where a third party plugs into multiple environments, and wreaks havoc if controls are not in place.
SecurityHQ have also seen similar occurrences with respect to a governmental client, in which a major vulnerability was exploited via a third party. In essence, a web application that was used for processing benefits, wasn’t sufficiently hardened, and was acting as a honeypot. This, naturally, attracted many bad actors, and put the organization’s payment systems at risk.
To manage third parties, organizations must have the ability to detect threats, and the capability to respond to them. Which requires the right combination of people, processes, and technologies.
Cost of a Cyber Breach
Regardless of the risk or cause, the cost of a data breach is monumental. According to IBM, ‘The average cost of a breach is $3.86 million dollars. This is a staggering amount of money for the average organisation.
We often become disassociated by statistics like this. But what the numbers show is that, while in past years the main concern was with avoiding reputation damage, now the main concern is avoiding complete devastation and company ruin. Cyber threats can now destroy an entire business in a matter of minutes.
For more information regarding the poll, or to speak with an expert, contact us here.












