Rewrites the Rule Book with Risk and
Incident Management Capabilities
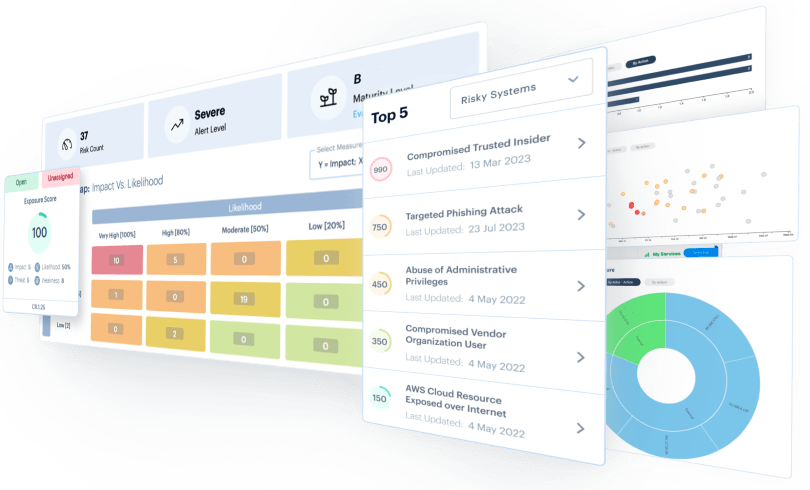
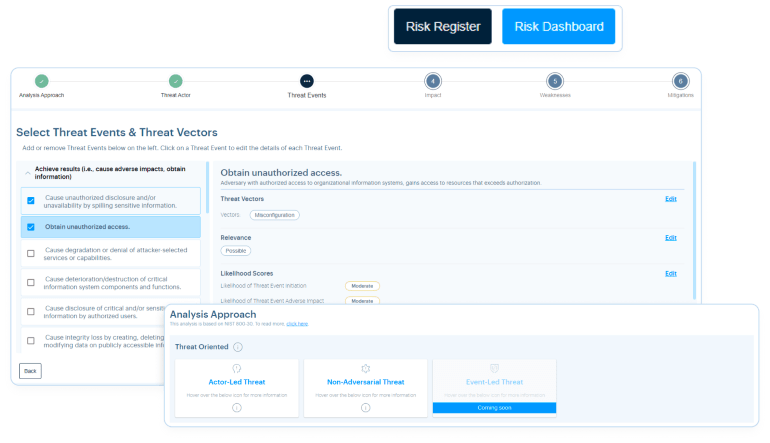
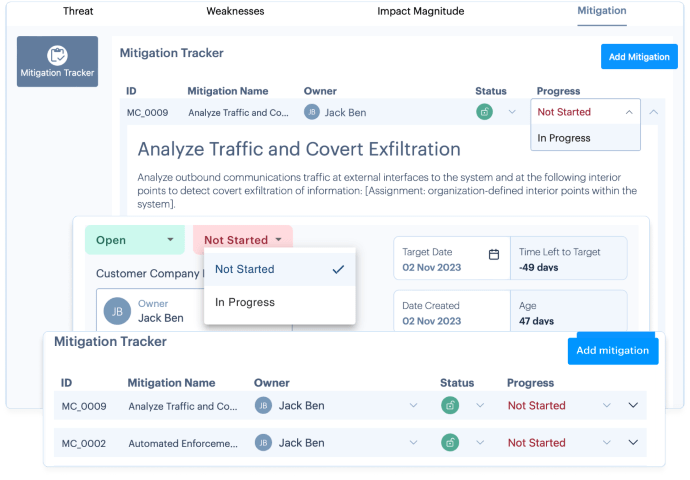
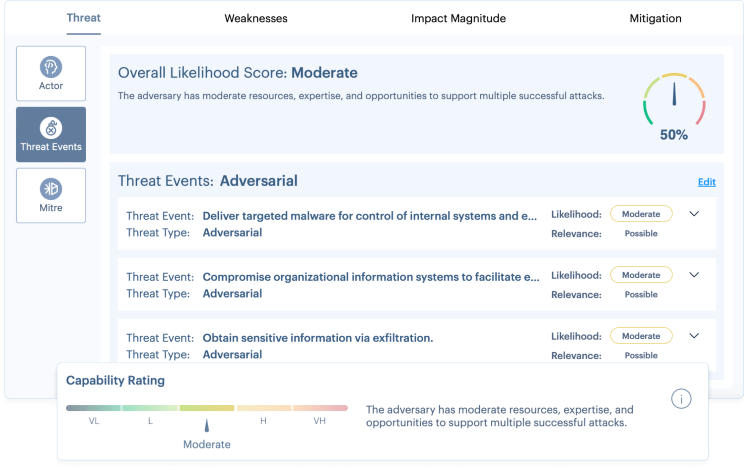
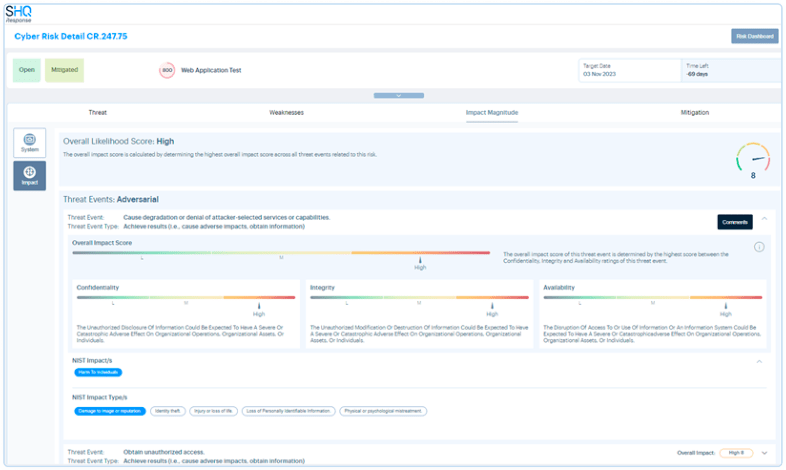
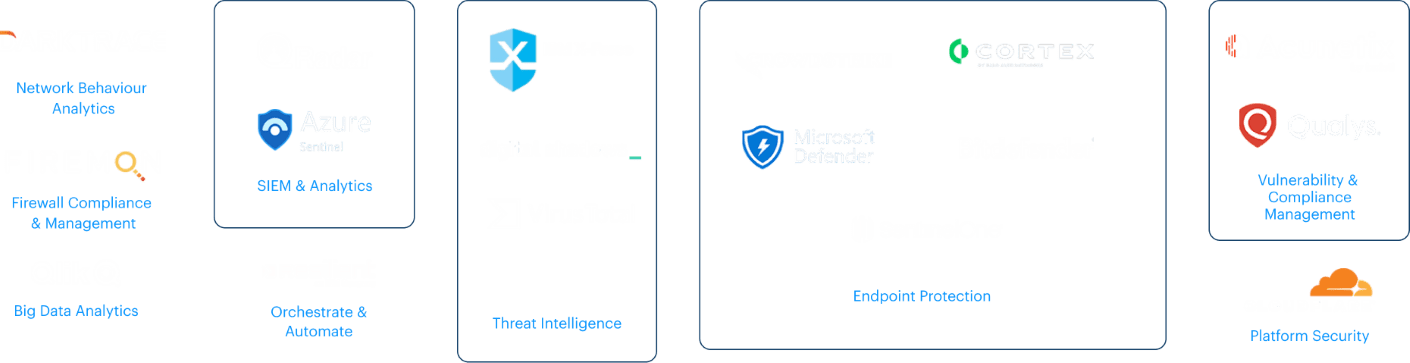
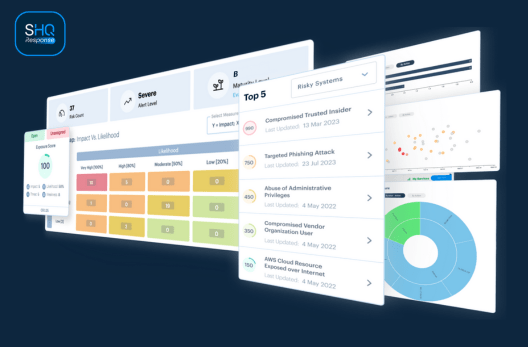
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.