Notes from the Field • 6 MIN READ
Using Favicon Hashes to Spot Vulnerabilities
by Prasad Dhole, Eleanor Barlow • Dec 2021
What is a Favicon?
If you take any modern browser, type any site into that browser, you will see an icon to the left-hand side appear by the pages title on the tab. It is this little icon that is known as a favicon icon. Favicon is shorthand for favourite icon. It is used as a shortcut to other webpages. Browsers that use these icons usually display them in the address bar, as well as in the history, and as bookmarks.
For instance, the red icon here representing the YouTube logo, is a favicon.

‘The favicon represents the identity of a website in a 16 × 16 pixels’ image file. It is also available in several different image sizes, such as 32 × 32, 48 × 48, or 64 × 64 pixels in size.’ – Kang Leng Chiew , Leverage Website Favicon to Detect Phishing Websites
Manipulating the Favicon Hash for Malicious Behaviour
A favicon can easily be accesses by taking the favicon.ico string on a website domain name. Take the BBC, for instance. Extract the domain name, so BBC.co.uk, place the favicon.ico icon at the end of the domain name, so that you will have bbc.co.uk/favicon/ico. Now, with this URL, you can place this into Google via an image engine to collect the relevant data.
This might appear to be an efficient trick. But this technique is a vulnerability issue that can be exploited by bad actors and hackers.
Attackers can hack into the favicon hash to redirect the path of a user. This way, a user may be clicking on the favicon with the intent of going to a specific site but may, in actuality, be directed to a bogus site abundant with malware. Once on this bogus site, the user may inadvertently download malicious code via phishing links, provide personal data/passwords/banks details, and more.
Although this method may be old, many people do not understand the utilisation of the favicon method as a means to infiltrate systems. They are evident throughout many F5 vulnerabilities. And, by acting as a hacker, we are able to report vulnerabilities to clients.
Real-Life Scenario Explored
Scenario: CVE-2020-5902 F5 BIG IP Load Balancer RCE/ Sensitive Path Disclosure vulnerability.
First, via google, we can find F5 BIG IP Load Balancer using inurl:/tmui/login.jsp
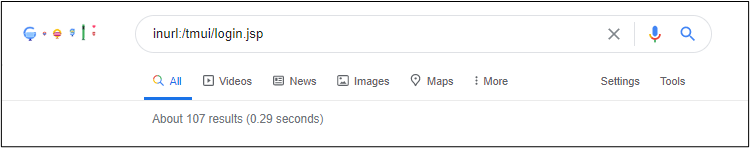
As you can see, we only have 107 results on google, which is not a lot. Acting as a potential hacker, we are going to use favicon method to increase our attack surface.
By going to the F5 site, we can see the favicon.
Now we must calculate the mmh3(murmurhash3) or favicon hash of the F5.
Below is a script, in which you will have to put the URL of the favicon, and it will show you the
https://github.com/Mr-P-D/Favicon-Hash-For-Shodan.io
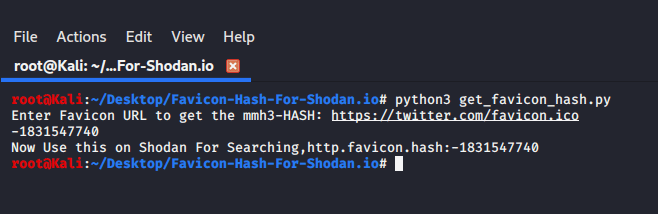
Using the hash generated, we can analyse the results below.
Another interesting use case of favicon is that we can identify subdomains which use the same favicon.
Here, for instance, Twitter is made apparent.
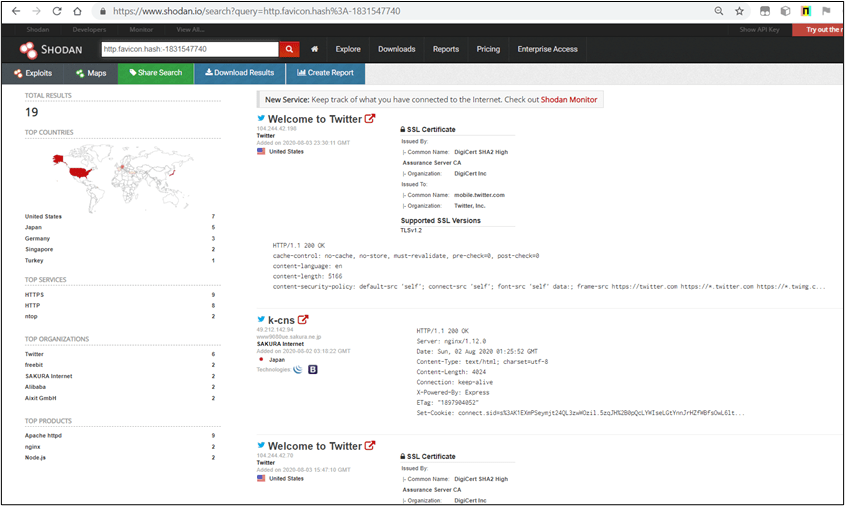
Getting the favicon hash of F5 BIG IP load balancer and using it with Shodan filter, like this, http.favicon.hash:-335242539 we can analyse the following.
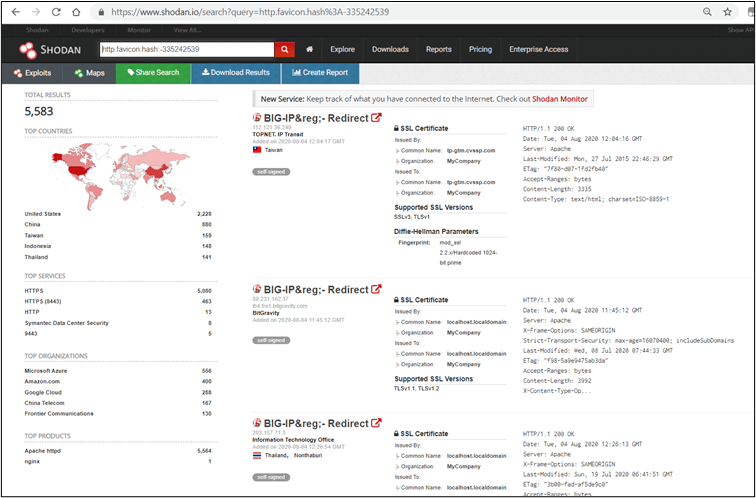
As you can see, we now have more than 5000 results of potential vulnerable applications to attack from. Note that in order to use Shodan filters (here, http.favicon.hash) you must be logged in.
In addition, if you select the favicon hash for each domain, IP or subdomain, you can then match those hashes with the fingerprints.json. If a favicon hash matches any fingerprints on those provided in fingerprints.json, then these can be used to hunt for known issues on webapps.
How to Safeguard Your Favicons
The favicon technique may be old, but these older elements are sometimes not acknowledged for the potential threat that it can be.
Recommended Actions
- Limit the number of favicons on your site. If you do not want your site to be discovered via favicon, it is best to reduce the number of them to as few as possible with regards to staging environments. Most of the search engines use favicon to identify sites. Only the external facing domain, which you want to be publicly shown, should have favicons.
- Employ the latest Vulnerability Management processes, and make sure to use Managed Detection and Response for complete visibility of your digital world, to visualise and understand malicious or anomalous activity, analysis, prioritise and respond to threats in rapid time. Safeguard your data, people, and processes.
If you enjoyed this blog, you may also find Using Proxy Logs to Detect Suspicious Activity useful.











