Infographics • 8 MIN READ
What is a Digital Footprint and How to Protect it?
by Vanashree Chowdhury, Eleanor Barlow, Anuja Chaudhari, Nilesh Burghate • Jul 2022
If you have an email ID, social media accounts, or ever made an online purchase, you have a digital footprint.
With every online activity, you leave traces of data behind. According to the Centre for the Protection of National Infrastructure (CPNI), a digital footprint is the data that’s left behind whenever a person uses a digital service, or when information about that person is published onto a digital forum, such as a social network. Not only is your digital footprint used by companies to show you targeted ads, but it can also be leveraged by attackers to gain information about you or your organisation to conduct targeted cyber-attacks such as phishing, identity theft, tailgating, and much more.
Organisations have a digital footprint too. This includes official social media accounts, domains, user account details, PR mentions, employee posts, internal working documents and so on.
With so much data at risk, you need to know how to protect your Digital Footprint, and the best way to do this is to follow the process outlined below.
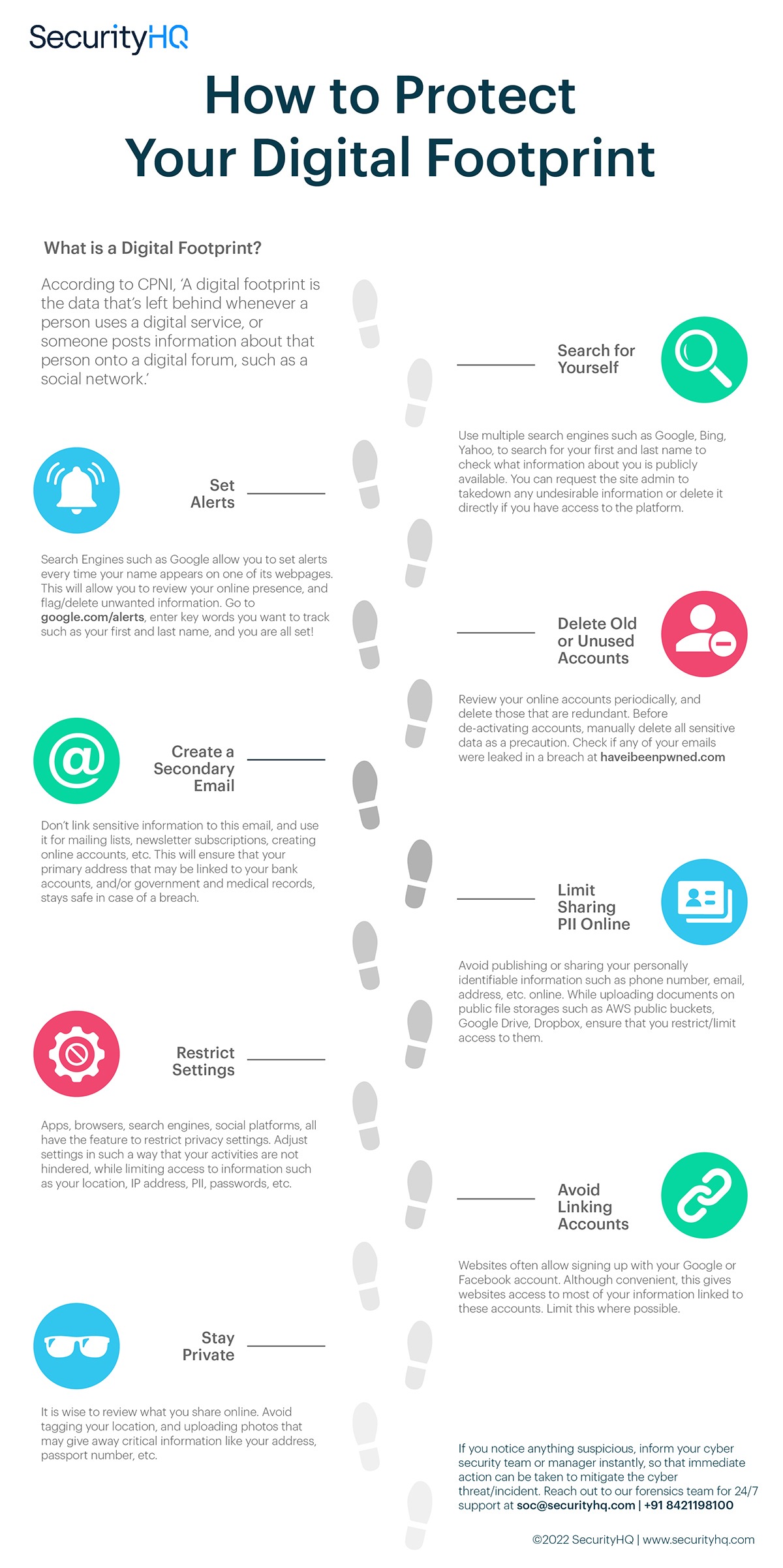
1. Search Your Digital Footprint
Use multiple search engines such as Google, Bing, Yahoo, to search for your first and last name to check what information about you is publicly available. You can request the site admin to takedown any undesirable information or delete it directly if you have access to the platform.
2. Set Alerts
Search Engines such as Google allow you to set alerts every time your name appears on one of its webpages. You can review your online presence, and flag/delete unwanted information. Go to google.com/alerts, enter key words you want to track such as your first and last name, and you are all set!
3. Delete Old or Unused Accounts
Review your online accounts periodically and delete those that are redundant. Before de-activating accounts, manually delete all sensitive data as a precaution. Check if any of your email accounts were leaked in a breach at https://haveibeenpwned.com
4. Create a Secondary Email Address
Don’t link any sensitive information to this email, use it purely for mailing lists, newsletter subscriptions, creating online accounts, etc. This will ensure that your primary address that may be linked to your bank accounts, and/or government and medical records, stays safe in case of a breach.
5. Limit Sharing of PII Data
Avoid publishing or sharing your personally identifiable information (PII) such as phone number, email, address, etc. online. While uploading documents on public file storages such as AWS public buckets, Google Drive, Dropbox, ensure that you restrict/limit access to them.
6. Restrict Settings
Apps, browsers, search engines, social platforms, all have features to restrict privacy settings. Adjust settings in such a way that your activities are not hindered, while limiting access to information such as your location, IP address, PII, passwords, etc.
7. Avoid Linking Accounts
Websites often allow signing up with your Google or Facebook account. Although convenient, this gives websites access to most of your information linked to these accounts. It is recommended to avoid such linkages to your email or social accounts.
8. Stay Private
It is wise to review what you share online. Avoid tagging your location, and uploading photos that may give away critical information like your address, passport number, etc.
Top Tips for Organisations to Safeguard Their Digital Footprint
1. Maintain A List of Registered Domains
Maintain a list of domains owned by your organization. Educate your IT Team/employees not to create any domain using corporate email account for personal use.
2. Beware of Typosquatting
Attackers are on the lookout for similar looking domains, like ‘.net’ instead of ‘.com’, which can be used to plan phishing attacks against said organization. To identify typo squatting or unintentionally similar domains, look up your organisation’s domain on https://dnstwister.report and block them at your firewall or proxy wall.
3. Search The Deep and Dark Web
Attackers often use the deep and dark web to share stolen credentials or sensitive information about organisations to plan cyber-attacks. Your Security Team should investigate the deep/dark web for suspicious mentions of your organization.
4. Check for Credential Leaks
Monitor the web for credential dumps related to your organisation and its employees. Keep an eye out for data leaks from large platforms such as LinkedIn, where your employees might have accounts. Instruct them to change passwords if you come across such a leak/breach. Finally, implement a Password Change Policy for all employees, especially ones with privileged access, or access to sensitive information.
5. Check For Open Ports
Continually monitor open ports on your public facing IPs available on the internet, for instance, your website, or services that are publicly accessible.
To give you an idea of what can happen when critical ports are left open, if port 3306 stays open, an attacker will be able to gain unauthorised access to your database. With open Port 22, a malicious actor can gain remote access to your system. To quickly look up open ports, run a search for your public domains and IPs on https://www.shodan.io/
Close open ports if not required. If your public facing IP or domain hosts a critical service, or admin control panel, and requires an open port for remote access, whitelist IP addresses for authorised users only.
6. Restrict Document Sharing
Restrict access to publicly accessible file sharing platforms on firewall or proxy so that employees are discouraged from uploading company documents. Documents shared on such sites can potentially be accessed by unauthorised users, causing data leakage.
While sharing confidential documents from your organisation’s official storage platforms such as Sharepoint, adjust ‘permission’ settings so that only intended users can access the data.
7. Delete Dormant Employee Accounts
If an employee leaves your organisation, immediately deactivate, or disable access to their accounts, especially those with privileged access. Accounts of existing employees that are no longer in use should also be either deactivated or disabled.
8. Onboard a Threat Intelligence Service
The first step is to identify your weak points, but the second and most important step is to take action to strengthen them. For this, you need advanced tooling, powered with automation and a team of expert analysts to identify, investigate, and mitigate weak spots, 24/7.
SecurityHQ’s Threat & Risk Intelligence (TRI) Service powered by Digital Shadows, harvests information available on the dark web, deep web, and the public domain, which is monitored 24/7 by our team of expert analysts to provide superior security and visibility to identify and highlight potential attacks, detect data breaches, and safeguard your organisation against ongoing and future threats.
Finally, if you notice any suspicious activity, inform your cyber security team or reporting manager instantly, so that immediate action can be taken to mitigate the cyber threat/incident. Reach out to our forensics team here.

![10 Tips to Protect Your Data [Infographic]](https://www.securityhq.com/wp-content/uploads/2021/07/Thumbnail-image-Tips-to-Protect-Your-Data-blog-copy.jpg)










