Cloud Security • 10 MIN READ
Security Implications of Cloud Digital Transformation
by Islam Rashad, Eleanor Barlow • Nov 2022
We are living in a highly data-driven world. Businesses and organizations are becoming more agile, productive, profitable, and competitive by the day. But in creating solutions to become more productive, profitable, and competitive, many issues equally arise.
What is Cloud Computing?
Cloud computing is the “on-demand delivery” of compute power, database storage, applications, and other IT resources, with the ability to scale out on a global scale to cope with any business growth requirements effectively.
“The world’s most valuable resource is no longer oil, but data” – David Parkins
How Can Public Cloud Services Benefit Organisations?
All public cloud service providers (CSP’s) such as Amazon AWS, Microsoft Azure, Google GCP, or Oracle OCI offer their cloud services in 3 main cloud computing flavours. These are designed to suit all different requirements, for any business or organization, looking to transform their IT estate to be fully on the cloud or to utilize some cloud computing services, and have a hybrid IT estate with a mixture of on-prem and cloud-hosted resources.
The Cloud Computing Flavors Are as Follows:
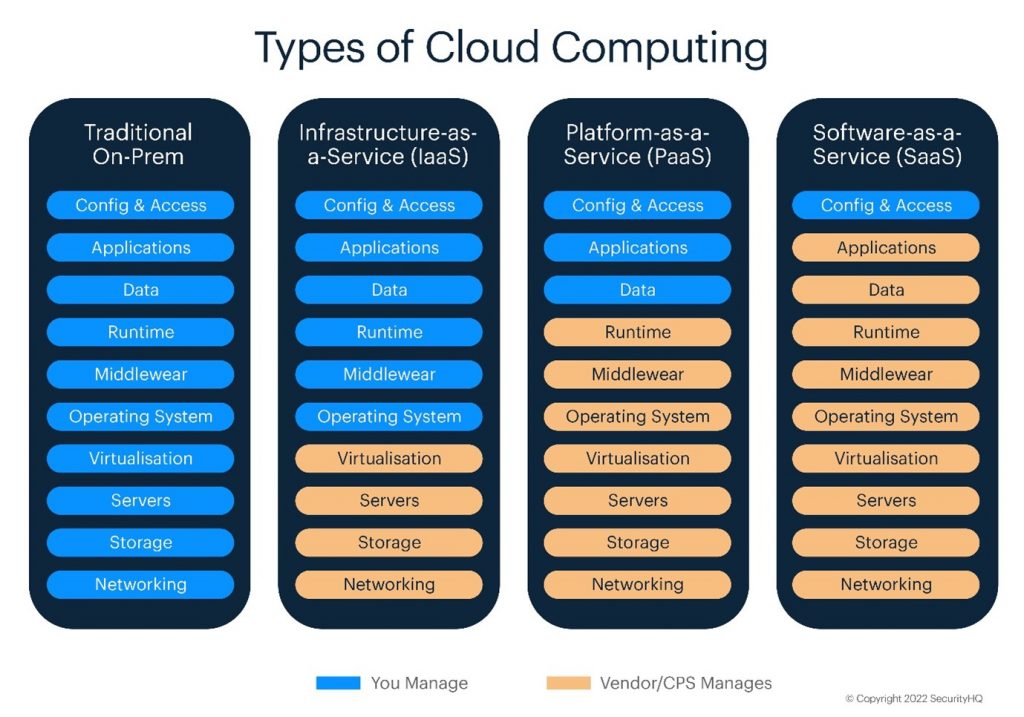
©2022 SecurityHQ
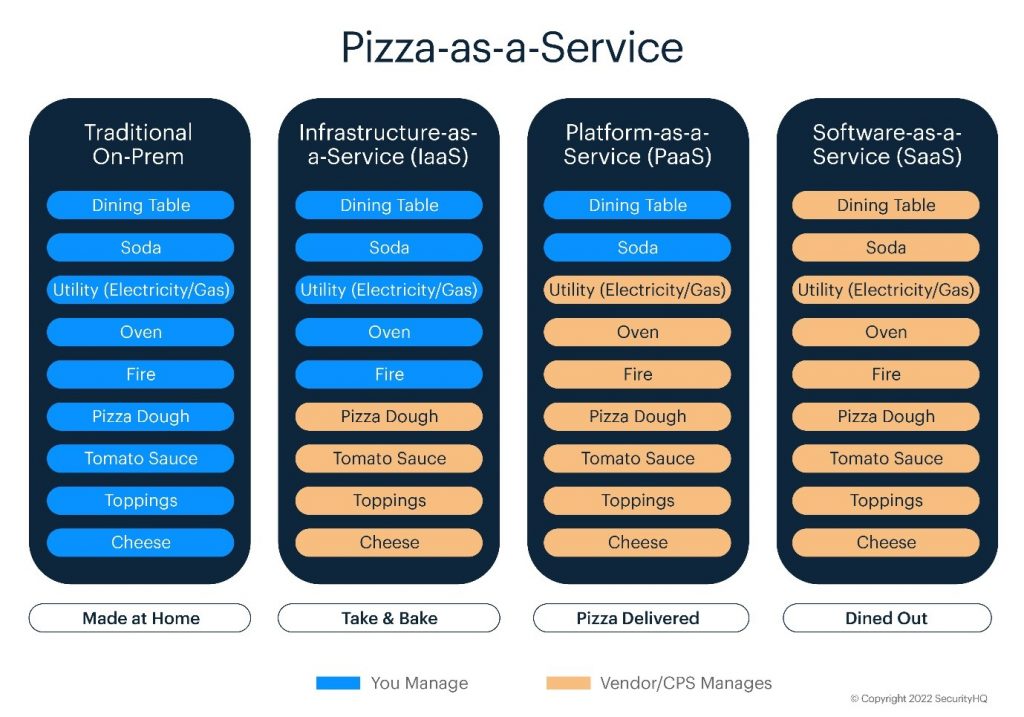
The “Pizza as a service” Analogy
There is great analogy explaining the core differences between each IT estate network & CSP service models (on-prem Vs. IaaS Vs. PaaS Vs. SaaS) that was first introduced by Albert Barron in 2014 called “Pizza as a service”:
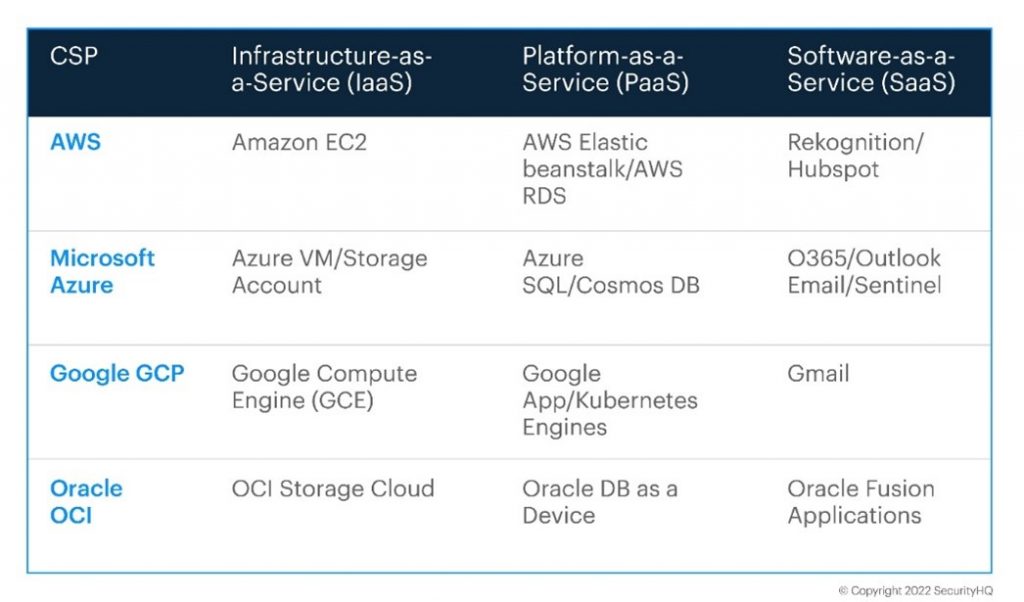
Examples of Cloud Computing Types
What Does Advancements in Cloud Mean for Security Teams?
From remote workforce transformation and business process developments to cloud-adoption, all these advancements have put a huge amount of pressure on security teams, and how they are able to secure modern interconnected IT environments. Environments that often compromise the security of hybrid systems, multi-cloud, SaaS applications and IoT/OT devices.
‘A change in Cloud configurations and administration means that there are many new opportunities for adversaries to detect vulnerabilities, and to exploit misconfigurations in Cloud environments.’- How MSSPs Are Responding to Cloud Acceleration
Adopting a cloud-migration journey means embracing a whole new level of unknown digital risk by shifting from the traditional trusted security model mostly based around the perimeter, to a new level of risk exposure “zero-trust” model by having your organizational resources hosted on a public cloud.
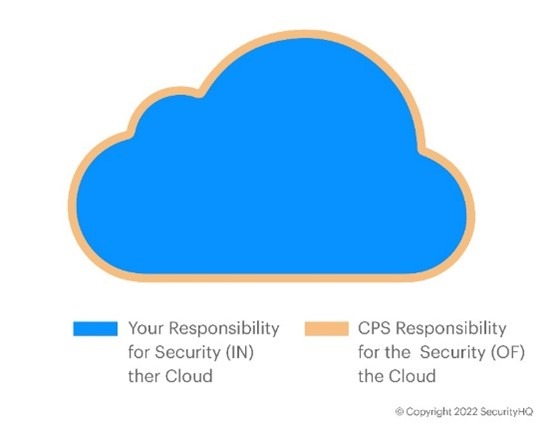
Cloud Security is a “Shared Responsibility” Model
It is extremely important for your security team to be fully aware of the cloud security shared responsibility model, in which you will always be responsible for the security of your data and applications sitting (IN) the cloud. While the CSP will always be responsible for the security (OF) of the cloud.
The Burden that Security Teams Have to Deal With
Over the last year or so most security teams have been left feeling overwhelmed with the amount of security challenges that must be delt with in rapid time. Especially when, amidst the constantly shifting threat landscape, ransomware groups and APT-sponsored attacks are at an all-time high.
These groups leverage a toxic mixture of malware, signature-based threats, along with a combination of highly evasive Tactics, Techniques, and Procedures (TTPs). Attackers are more determined than ever, and inflict the maximum amount of harm, while remaining undetected, almost invisible, for extended periods of time.
Top Cloud Related Challenges to Security Teams
- Lack of skilled security staff to handle Cloud Security properly.
- Lack of resources to build 24×7 SOC monitoring to secure your Cloud (IaaS/PaaS) workloads, SaaS applications and other on-prem assets properly.
- Lack of having a prompt incident response measure to threats targeting Cloud related vulnerabilities.
Top Tips to Prevent Cloud Related Vulnerability Exploitation
- Establish a comprehensive pervasive level of visibility across your estate, whether it consists of on-prem, Cloud or a mixture of both type of assets.
- Work towards having a “Single Pane of Glass” view by establishing a comprehensive pervasive level of visibility across your estate, whether it consists of on-prem, endpoints, Cloud or a mixture of different type of assets. This can be done using log-based analytics and API-driven integrations on a SIEM.
- Improved Digital Risk controls based on measurable metrics (SOC KPI’s, tickets generated/resolved and service SLA’s) and risk assessments.
Platform as a Service (PaaS) has simplified the delivery of services, but you are still left accountable for the security of those services hosted in Microsoft Azure, Amazon Web Services and Google Cloud Computer. View this webinar recording on ‘How to Hunt Threats in Azure & AWS PaaS Services’ to learn more tips and tricks when using Cloud.
Having conducted incident response investigations across a wide range of industries, SecurityHQ are best placed to work with businesses large and small, and across numerous technical environments to reduce the impact of a cyber security incident. For more information on these Cloud related threats, speak to an expert here.



![10 Tips to Protect Your Data [Infographic]](https://www.securityhq.com/wp-content/uploads/2021/07/Thumbnail-image-Tips-to-Protect-Your-Data-blog-copy.jpg)








