Notes from the Field • 10 MIN READ
7 Types of Social Engineering Attacks Targeting You
by Vanashree Chowdhury, Eleanor Barlow, Anuja Chaudhari • Feb 2023
Social Engineering, in Information Technology (IT) Security, is a non-technical cyberattack tactic that uses psychological manipulation to gain confidential information, unauthorized access or valuables from a person or organization.
‘Social engineering does something all other attempted technical attacks cannot: it gets into your head.’ says IBM.
Common Types of Social Engineering Attacks
There are various forms of Social Engineering attacks which are used to target businesses. The majority will aim to do this by targeting and exploiting individuals within the targeted organisation.
Here are 7 of the most common types, how they work, and how to handle them.
1. Phishing
Phishing is where an attacker attempts to contact users via email, telephone, or text, appearing as a trusted or legitimate source. The aim is to trick users into revealing login credentials credit card details, click on malicious links, or download malicious files.
Phishing attack types include:
- Spear phishing, where the attack is targeted toward a specific person or group of people.
- Vishing involves fraudulent voice messages or calls.
- Smishing, also known as SMS phishing, uses text messages to lure victims.
- Whaling, wherein a perpetrator takes on the guise of a senior member in the organisation to target employees with privileged access.
How to Avoid a Phishing Attack: View this Infographic on top tips to recognise one!
2. Baiting
A ’bait’, be it digital or physical, is laid out to entice a user. It may be in the form of an interesting movie download, or a USB drive with an intriguing label such as ‘Employee Appraisals’ that is surreptitiously placed on a desk. Once an unsuspecting user downloads the bait, malicious software is delivered directly into the end user’s system.
Recommendation to Avoid a Baited Trap: Never use any physical application/USB/CD etc or click on any download/link without being certain of its origin. If in doubt, leave it out. Look at this Infographic on securing portable devices for more.
3. Pretexting
The purpose of pretexting is to build a relationship/level of trust with the victim before an attempted attack is made. It is used by the bad actor to create a pretext, or a story, to gain trust with an individual, who they later manipulate to gain key information or data. Often, the attacker poses as a co-worker or an authoritative figure.
Recommendation to Avoid a Pretext Scam: Keep personal data/account details close to your chest. Be especially wary of people wanted to get to know you/relate to you over calls, and strangers being overly friendly. Treat every new call with an unknown person as a potential pretext scam.
4. Quid Pro Quo
Quid Pro Quo, a term when used in cyber security, refers to a combination of tactics used in Pretexting and Baiting whereby an attacker poses as a trusted source and may ask for otherwise inaccessible information in exchange for a gain or offer. The purpose of this is to lure the person into sharing details, rather than pressuring/ scaring them into disclosing information.
A recent example of this can be see where the cybercrime group that goes by the name of FIN7, created a bogus security company, that went by the name of Bastion Secure. The company claimed to provide penetration testing services for private companies and public sector organizations across the world. They then hired security researchers and tricked them into contributing towards ransomware attacks. According to The Record ‘The attacks installed ransomware such as Ryuk or REvil, two ransomware strains that have been tied in recent years to FIN7 attacks, according to Gemini Advisory.’
Recommendation: Same as avoiding a pretext scam, keep personal data/account details close to your chest. Be especially wary of people wanting to get to know you/relate to you over calls, and strangers being overly friendly.
5. Water-Holing
Water-Holing is usually targeted toward users belonging to a specific group or industry and is used to infect websites that are typically frequented by the target users. The users may then click on malicious links on the website they usually use (or a bogus website set up to emulate the real site). Once malware is downloaded from the malicious link, this may provide attackers with access to the victim’s machine and network.
A study by Google researchers found that up to 90% of all domains involved in distributing fake antivirus software used social engineering techniques.
Recommendation to Avoid Water-Holing Attack: Do not click on any links that are not necessary and that don’t have the right security measures in place to detect malicious activity.
6. Tailgating or Piggybacking
Also termed as piggybacking, tailgating is when an attacker poses as someone trustworthy and physically follows an authorised person into a restricted corporate area. The attacker might ask the victim to leave the door open, claiming to have misplaced their access card, or be part of a delivery team. This method can be used as a catalyst to physically steal information from an organization which can then be used as part of a ‘Baiting’ attack.
Recommendations to organisations: Ensure that robust security measures are in place, always, at all entrances/exits. Ensure multifactor authentication is needed for entry where possible, and different forms of authentication are used in more sensitive areas within the same building.
7. Mind Games
A SecurityHQ employee, responsible for conducting voice-phishing (vishing) simulations for a client, shared that they were successful in retrieving confidential data from victims 100% of the time when they appealed to the human side. The SecurityHQ employee stated that ‘I did this by pretending like I didn’t really understand how the process worked. A sense of urgency played to my advantage, as I stressed that the data I was requesting, was for a client meeting scheduled minutes from the vishing call’.
Recommendations: As part of our services, SecurityHQ conducts phishing simulations for our clients. Our insights thus far show that at least 37.25% of receivers opened phishing emails, around 18.25% clicked on links and 16% submitted confidential or sensitive data.
How Awareness Helps Prevent a Cyber Attack
Interestingly, when one of our own SecurityHQ employees received an email seemingly from our CEO (CEO Fraud), asking for documents urgently, he was immediately able to identify it as a phishing email by spotting the suspicious email ID of the sender and subsequently reported it to our investigations team to curb the attack before it could spread. This was a result of Cyber Awareness trainings conducted regularly in our organisation.
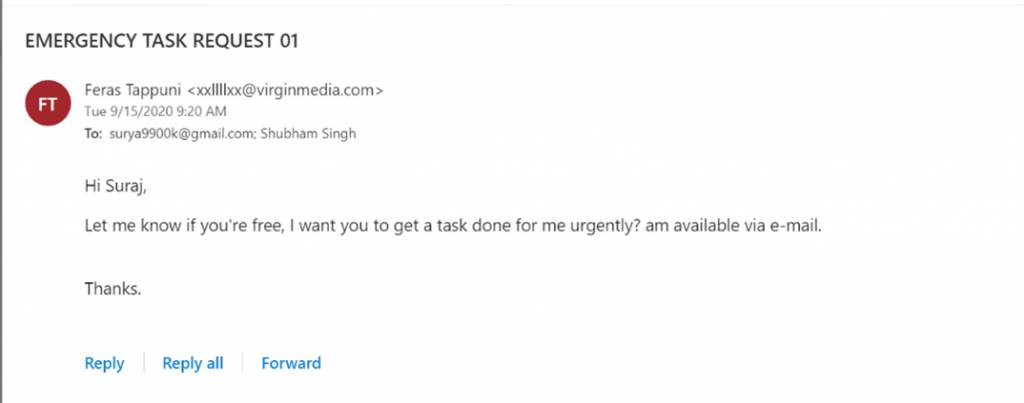
Download this webinar on ‘Tips to Educate and Protect Your Staff from Security Threats’.
Or, to speak with a security expert, get in touch with the team.








