Industry Insights • 10 MIN READ
Code of Conflict: The Global Cyber Divide Between Gaza and Israel
by Patrick McAteer • Oct 2023
The escalation of tensions between Gaza and Israel in recent weeks has reached unprecedented levels, attracting acting worldwide attention like never before. This conflict has brought about a new battle line, one that only in recent years has become a pillar to modern day warfare.
While the bulk of the fighting is taking place on the ground and so far, been kept closed off to the region, the cyber war has begun to stir and expand worldwide. For years, nations have been putting one another’s cyber defence systems to the test, the difference here is the mass international involvement from groups located far and wide joining the digital fight.
Silent Sabotage
Similar to the further escalation of the Russia-Ukraine war that began almost two years ago, threat groups, individuals and other APT’s have used this chance to exploit various realms across the cyber field. Each with their own motive for joining the fight and idea of what they aim to get out of it.
Some join for their own personal amusement, others for monetary gains, but the majority have joined for the political reasons embedded in this deep-rooted conflict. Just days after Hamas entered Israel on October 7th, we observed a significant increase in the number of threat actors that began to align with one side or the other which, in turn, has also caused a significant increase in the number of cyber-attacks occurring in the region and around the world.
As of right now, there have only been a few serious cases, with the majority causing minimal damage. There are however a few possible developments which could lead to heavier consequences than what we have seen so far. With Russian, Iranian, Indian, and other nation backed groups recently entering the fray.
Disruption Dilemma
Since the outbreak of the current conflict, DDoS (Distributed Denial of Service) has overwhelmingly dominated the landscape of cyber-attack methods being used. While most incidents have resulted in limited damage, we observed instances where overwhelming traffic managed to prevent access to various Palestinian/Israeli government, media, finance, telecommunication, and critical infrastructure websites. These, however, are not permanent solutions, as they last only several minutes or hours.
DDoS has not been the exclusive attack method throughout this conflict; with cases of website defacement and general vulnerability exploits also taking place. During the initial attack, a mobile app that alerts Israeli civilians of incoming rockets known as “Red Alert: Israel” had a vulnerability exploited. This allowed the hackers to not only intercept alert requests, but also to dispatch fake ones including one that said, “nuclear bomb is coming.” With thousands more downloading the various warning applications after the drastic influx of rockets, it was also revealed that malicious versions posing as the official “RedAlert” application were being installed all over Israel. After a few days they had obtained access to sensitive information from both iOS and Android stores belonging to over 100,000 users. The sophisticated spyware within took code from the authentic RedAlert application, but requested further access to the user’s Contacts, Call Logs, Phone IMEI, SMS Messages, list of Installed Software, Logged in Email, other App Accounts and more.
Attacks from sympathizers on both sides of the conflict have caused varied levels of disruption over the past few weeks. For now, the damage has not escalated to much more than websites in both the public and private sector being taken down, defaced or various other exploits being taken advantage of. With the number of groups continuing to expand, there seems to be a sudden surge in malicious activity which places an increased number of organisations at risk. Below is a brief list of some prominent activity that has taken place:
The Jerusalem Post by Anonymous Sudan
The Jerusalem Post, shown below, by Anonymous Sudan which was down for over 2 days.
Anonymous Sudan Statement: ‘+50 hours and the website is still down.’
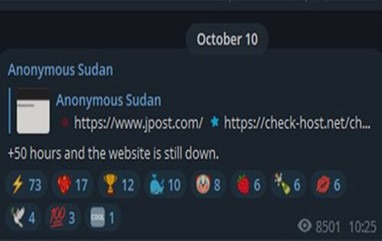
Figure 1: Source: Anonymous Sudan Telegram Channel
The Israeli Government Website by Killnet
Killnet Statement: “Government of Israel, you are to blame for this bloodshed,” Killnet said. “Back in 2022, you supported the terrorist regime of Ukraine. You betrayed Russia. Today Killnet officially informs you about it! All Israeli government systems will be subject to our attacks!”
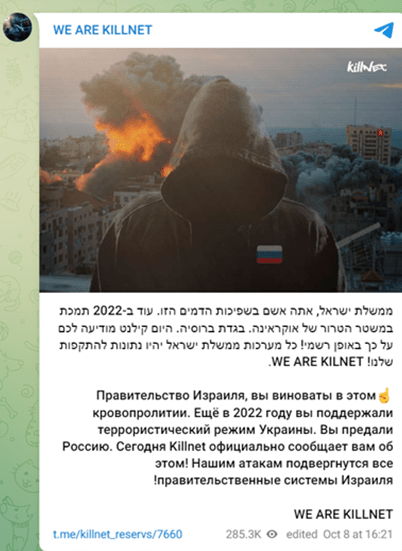
Figure 2: Source: WE ARE KILLNET Telegram Channel
RedAlert Application by AnonGhost & Anonymous Sudan
Anonymous Sudan: “Tzevaadom” application and the “RedAlert” application are currently unavailable. There are the alert applications in Israel.”
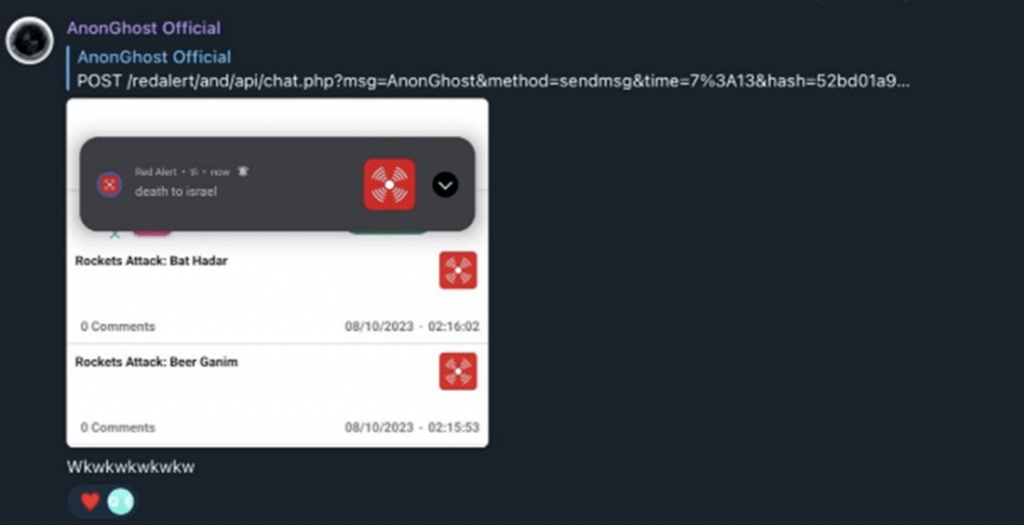
Figure 3: Source: AnonGhost Official Telegram Channel
Figure 4: Source: Anonymous Sudan Telegram Channel
Threat Groups Development
Although the conflict is contained to a small section of the Levant region, the overwhelming mass mobilization across the world has helped draw a much larger picture of the political landscape rapidly unfolding. Cyber groups worldwide have pledged their services to varying sides, with the majority siding alongside the Pro-Palestine or Anti-Israel banner. Many seem to be following the path that their nation takes, with Pro-Russian groups like “Killnet” taking up digital arms against Israel and groups based out of Israeli allied nations like “Kerala Cyber Xtractors” in India hitting Palestine. From state backed threat actors to individual hacktivists, the wide variety of groups is increasing day by day and does not seem to be slowing down.
The battleground does not stop at the borders of just these two nations though, with cyber-attacks from either side targeting critical infrastructure, military targets, governments, and private organisations of countries that are aligning with the opposing side. Nations with Pro-Palestinian hacktivists have set their sights on nations such as USA, UK, Germany, India, France, Italy, Canada and more over recent weeks. Likewise, various Pro-Israeli hacktivists have targeted, Iran, Iraq, Qatar, Saudi Arabia, and Lebanon.
With the list of threat groups is ever changing, here are the current known groups that are actively participating, the side of the conflict they chose to align with and their preferred attack vector.
List Source: Israel-Palestine Cybertracker – Cyberknow
| Pro-Israel Group | Speciality |
| AnonyMiss | DDoS |
| Anonymous India | DDoS |
| Ares | Data Leak |
| Dark Cyber Warrior | DDoS |
| Garuna Ops | DDoS |
| Gaza Parking Lot Crew | Hack |
| Glorysec | Hack |
| Indian Cyber Force | DDoS/Hack |
| Israel Cyber Defence | DDoS |
| Kerala Cyber Xtractors | DDoS |
| Op Iran | DDoS/Hack |
| Predatory Sparrow | Hack |
| Red Evils | DDoS/Hack |
| Silencers of Evil | Hack |
| SilentOne | DDoS |
| Team UCC Operations | DDoS |
| Termux Israel | DDoS/Hack |
| Pro-Palestine/Anti-Israel Group | Speciality |
| 1915 Team | DDoS |
| 313 team | DDoS |
| 4 Exploitation | DDoS |
| ACEH | DDoS/Hack |
| AnonGhost | DDoS |
| Anonghost Indonesian | DDoS |
| Anony_Mous | DDoS |
| Anonymous BD | DDoS |
| Anonymous Morocco | DDoS |
| Anonymous Sudan | DDoS |
| Arab Anonymous Team | DDoS |
| Ben M’Hidi 54 | DDoS/Hack |
| Black Security Team | DDoS |
| Blacksec | DDoS/Hack |
| Blackshieldcrew MY | DDoS |
| Boom Security | DDoS |
| C.O.A Agency | DDoS |
| Cscrew | DDoS |
| Cyb3r Drag0nz | DDoS |
| Cyber Army Palestine | DDoS |
| Cyber Av3ngers | Hack |
| cyber sederhana team | DDoS |
| Cyber System Error | DDoS |
| Dark Strom Team | DDoS/Hack |
| Darkseek Hacking Group | DDoS/Deface |
| DevilAttacks | DDoS |
| Dragonforce Malaysia | DDoS/Deface |
| Eagle Cyber Crew | DDoS |
| Electronic Tigers Unit | DDoS |
| End Sodoma | DDoS/Hack |
| Esteem Restoration Eagle | DDoS |
| Fallaga Team | DDoS |
| Ganosec team | DDoS |
| Garnesia Team | DDoS |
| Garuda Security | DDoS |
| Gb Anon 17 | DDoS |
| Ghost Clain Malaysia | DDoS |
| Ghost Princess of Palestine | DDoS |
| GhostClan | DDoS |
| Ghosts of Palestine | DDoS |
| Ghostsec | Hack/Ransomware |
| Hacktivist Indonesia | DDoS |
| Haghjoyan | DDoS |
| Hizbullah Cyb3r Team | DDoS |
| HostKillCrew | DDoS |
| Infinite Insight.ID | DDoS/Hack |
| IROX Team | DDoS/Hack |
| Islamic Hacker Army | DDoS/Deface |
| karawang cyber team | DDoS |
| Kep Team | DDoS |
| Ketapang Grey Hat Team | DDoS |
| Khalifah Cyber Crew | DDoS/Deface |
| Killnet | DDoS |
| Komandan Hansip | DDoS |
| kuningan Exploiter | DDoS |
| Lulz Security Agency | DDoS |
| Moroccan Black Cyber Army | DDoS |
| Moroccan Ghosts | DDoS |
| Moses Staff | Hack |
| Muslim Cyber Army | DDoS |
| Mysterious Silent Force | DDoS |
| Mysterious Team Bangladesh | DDoS |
| Night Raid Cyber | DDoS/Hack |
| Ox Web Moroccan | DDoS/Deface |
| Pakistani Leet Hackers | DDoS |
| Panoc team | DDoS |
| PMOI | DDoS Hack |
| R4gn4r0k Ghost | DDoS |
| RuBit | DDoS |
| Skynet | DDoS |
| Soldiers of Solomon | Ransomware |
| StarsX Team | DDoS |
| Storm-1133 | Hack |
| Stucx Team | DDoS/Dox |
| Sylhet Gang-SG | DDoS |
| SynixCyberCrimeMY | DDoS |
| Team Azrael Angel of Death | DDoS |
| Team Herox | DDoS |
| Team_insane_Pakistan | DDoS |
| Team_r70 | DDoS |
| Tengkorakcyber | DDoS |
| The Cyber Watchers | DDoS/Hack |
| The Returnees | DDoS/Deface |
| ThreatMiltiy | DDoS |
| Tunisian Cyber Army | DDoS |
| TYG Team | DDoS |
| US Nexus Networks | DDoS/Hack |
| Usersec | DDoS/Deface |
| Vulzsec | DDoS/Hack |
| Weedsec | DDoS |
| Xecatsha | Hack |
| Xv888 | DDoS |
| YourAnonT13x | DDoS |
Threat Intelligence for the Future
SecurityHQ’s Threat Intelligence team is a cohesive global unit dedicated to Cyber Threat Intelligence, focused on researching emerging threats, tracking activities of threat-actors, ransomware groups, and campaigns, to ensure that they stay ahead of potential risks. Beyond their investigative work, the Intelligence team provides actionable threat intelligence and research, enriching the understanding of SecurityHQ’s customers worldwide. United by a common commitment, the SecurityHQ Threat Intelligence team delivers the insights needed to confidently navigate the intricacies of the cyber security threat landscape.
For more information on the threats mentioned in this blog, speak to an expert here. or if you suspect a security incident, you can report an incident here.