Cloud Security • 10 MIN READ
Charged Risks: Vulnerabilities in Electric Vehicle Charging Infrastructure Exposed
by Tim Chambers, Eleanor Barlow • Jan 2024
The Electric Vehicle (EV) industry has hit full speed, with the UK government pledging that all new cars will be zero emission by 2035. According to the European Environment Agency, the European bloc has followed suit, with 22% of passenger vehicles being electric in 2022.
Home Charging Issues
The below image highlights one of the most popular EVs, being charged with a generic home charger. This shows the use of the vulnerable SNMPv1 protocol being used (the MAC address has been redacted). A low-level malicious actor could use this information to initiate a Denial of Service (DoS) or attempt to modify the internal systems of the car.
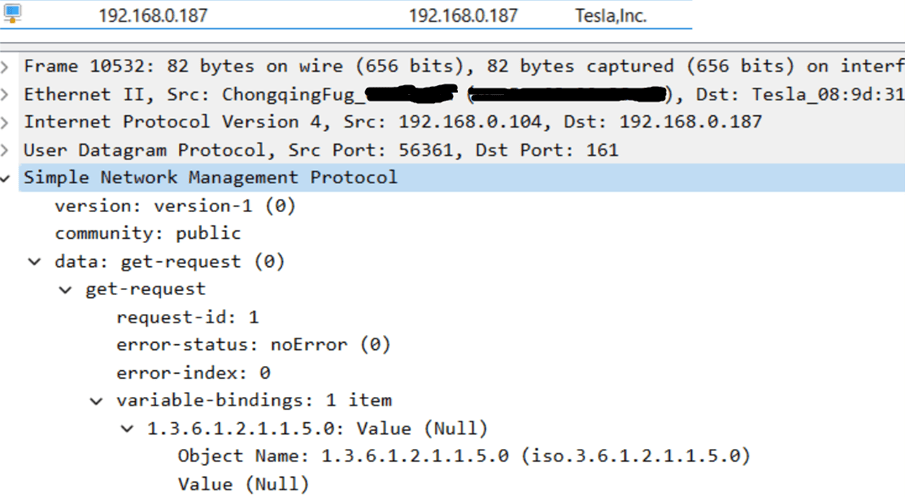
Whilst EV manufacturers have stressed that their cars are secure, the use of such protocols is indicative of a reactive approach to cybersecurity, patching vulnerabilities when found, as opposed to being secure by design. The use of a protocol invented in the 1980s in a car that is widely seen as the future of human transport, sets a less than perfect precedent.
With EVs leading the way to a greener future, many insiders in the industry have raised the alarm about the inherent vulnerabilities and implications of having vehicles which are not just ‘smart’ and ‘networked’, but in fact, an entire auto industry hooked up to a global network that has already been the target of malicious actors across the globe.
Issues with Moving Forward Safely
Many EV manufacturers publicise their bug bounties, which is a step in the right direction. With more and more business understanding the inherent cyber risks when operating in such a space; such operational practices will inevitably lead to strategic changes in risk appetite and cyber attitudes. However, the prevalence of overarching NDAs, and a rapid development cycle has led to several key flaws becoming apparent.
Primary Mode of Transport
The first consideration is that a fleet of EVs becoming the primary mode of transport would completely overhaul the traditional petrol station infrastructure that has been commonplace for decades. Instead, scores of electric charging stations will become the norm, with EVs drivers ‘charging’ their tanks instead of filling them up. This would comprise a large network of cloud computers which would build a ‘grid’ or EV chargers across the world.
Many of these grids would be owned and operated by separate entities, with budgetary factors being the driving force when it comes to security concerns. The Colonial Pipeline breach of 2021 illustrated how damaging core infrastructure breaches can be, and this will only be multiplied if such an attack was to impact a more interconnected and less secure global asset, cutting over half of the fuel to the American East Coast.
Centralised Store for all Crucial Data
Many readers may already have concerns about a highly centralised store of all automobile information, with encryption keys for vehicles and payment information. Such a glut of sensitive information being held in an emerging industry underpins the importance of secure design.
Exposure to Nation State Threats
A co-ordinated nation-state attack triggering a DDoS is no longer the work of science fiction; with an entire electrical grid being networked and partially exposed over the internet, Nation State Actors will keep on monitoring for vulnerabilities, and take advantage of these when found.
Internal Impact of Operational Technology
Networked Operational Technology (OT) impacts business and consumers similarly, as offices in the EU have started to have dedicated chargers outside their buildings, which is connected to a part of their corporate network. This, of course, can be used to pivot to an internal closed network, with several home users already reporting their home Wi-Fi being hacked and financial information stolen, after installing a home EV charger.
Enabling Better Cyber Security for Electric Vehicles
The inevitable data privacy concerns that come with having personal user data residing on business networks, which can never be considered truly secure, may become a regulatory headache for risk officers. Many enterprises will need to seriously consider if such ‘green’ infrastructure may bring their company more harm than good.
A Penetration Test aiming to leverage any potential risks posed by emerging technologies, would certainly be the first step. Navigating the regulatory concerns that this will likely lead to, is something that businesses need to certainly consider.
There are many EV charging companies, who provide environmentally friendly infrastructure, in an emerging market globally. But if breached, it is likely that this will not only impact consumer confidence in their business, but perhaps in the EV revolution itself.
Next Steps
At SecurityHQ, we understand the complex and critical infrastructure of the industry. Our Threat Intelligence team is a cohesive global unit dedicated to Cyber Threats Intelligence, focused on researching emerging threats, tracking activities of threat-actors, ransomware groups, and campaigns, to ensure that they stay ahead of potential risks. Beyond their investigative work, the Intelligence team provides actionable threat intelligence and research, enriching the understanding of SecurityHQ’s customers worldwide. United by a common commitment, the SecurityHQ Threat Intelligence team delivers the insights needed to confidently navigate the intricacies of the cyber security threat landscape.
If you want to identify and protect your business from prevalent cybersecurity threats, schedule a consultation with our experts today.