Rapid Response to Contain Threats and Limit Damage.
Orchestrate Containment Across Multiple IT Systems, On-prem or Cloud.
Track Containment Actions with Other Incident Response Actions.
Change Credentials to Take Containment Actions Any Time on Your Own.
You need to be fully prepared to trigger containment actions if breached.
Rather than sit and wait for the damage to be done, Contain-X Connector is an extension of our Security Orchestration, Automation & Response (SOAR), that automates threat containment actions to restrict threats, speed up and support incident response, in rapid time.
Contain-X Connector supports the most highly used security technologies for containment actions such as:
Contain-X Connector Works as an Add-on Module to Managed Detection and Response (MDR)
Contain-X Connector Service Features
Hardened System
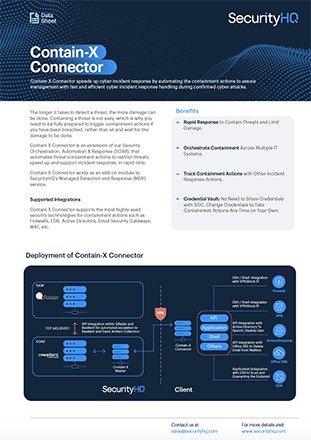
- Contain-X Connector is installed on hardened OS, and monitored 24x7 for suspicious activities by SOC. It accepts connections only from Contain-X Master
Data Transmission
- Transmission of credentials and commands happens over an encrypted channel using latest TLS v1.3 protocol.
Small Footprint
- Contain-X Connector can be installed on small virtual machines with minimum resources and restricted network access.
Deployed in the Customer Network
- Contain-X Connector is deployed in the customer network, to prevent unnecessary exposure to the internal network from the MSSP network.
Credential Storage
- Credentials required for taking actions are stored in encrypted form on Contain-X Connector, using AES-256-GCM on the client side.
Uptime and Security
- SOC monitors uptime and security of Contain-X Connector on 24x7 basis and is responsible for monitoring and management.
Get in Touch!
Experience the benefits of Contain-X Connector.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.