Cyber Defense Center
Threat Actors Leveraging Phishing to Compromise User Mailbox and Abuse Inbox Rules
Detection: SecurityHQ’s SOC detected suspicious email activity associated with a user account, including abnormal inbox rule creation and unusual outbound email patterns, through Microsoft Defender for Office 365 alerts and message tracking log analysis.
Description: SOC identified a phishing incident where a user’s credentials were compromised after interacting with a malicious phishing email. Following successful account compromise, the threat actor authenticated to the user’s mailbox and created a malicious inbox rule that automatically forwarded incoming emails to an external RSS feed email address and marked those emails as read, effectively hiding attacker activity and exfiltrating sensitive communications.
Further investigation revealed that the compromised user account was subsequently used to send internal phishing emails to multiple employees within the organization, leveraging the trust associated with a legitimate internal sender. As a result, several additional user accounts were exposed and partially compromised before containment actions were initiated. Lead Incident Responder reviewed audit logs, inbox rule configurations, sign-in activity, and email telemetry to confirm the scope of compromise and identify affected users.
Immediate response actions included disabling the compromised account, resetting credentials, removing malicious inbox rules, revoking active sessions, and blocking the external forwarding destination. All affected users were notified, and suspicious internal phishing emails were removed from mailboxes using Defender remediation actions.
Lessons Learnt: User phishing remains a highly effective initial access vector for attackers. Inbox rule abuse is a common technique used to maintain persistence and evade detection. Rapid detection, user education, and automated remediation capabilities are critical to minimizing the blast radius of phishing-based compromises.
Threat Actors Exploiting weakness in ASP.NET viewstate deserialization to Remote Code Execution
Detection: Client reported possible malicious activity due to the presence of web shells on an IIS-hosted web server.
Description: The client reported the possible presence of a web shell on a web server. The team initiated an investigation using the available IIS server access logs and requested access to the client’s Microsoft Defender console. Based on log analysis, the team confirmed that the initial attack vector was an ASP.NET ViewState deserialization vulnerability. The team identified all malicious web shell payloads and the source IP addresses from which they were deployed. Immediate mitigation steps were recommended, including removing write permissions from the utilities folder. The team also provided all identified Indicators of Compromise (IOCs) to be blocked via the Defender console.
Recommendations: To strengthen the overall security posture, the team recommended applying the patch for the ViewState vulnerability. The team provided all available Indicators of Compromise (hashes) to be blocked in Microsoft Defender and also shared detection criteria for identifying similar instances, recommending the creation of a custom detection rule in Defender.
Lessons Learnt: Organizations should patch zero day critical vulnerabilitites immediately. IIS web servers hosting public applications are attractive targets for attackers. Continuous monitoring and hardening of these assets are essential. Enforcing least-privilege access (e.g., restricting write access to application folders) can significantly reduce attacker capabilities.
Threat Detection Engineering
Key Detection Engineering Highlights for December
A Global Penetration Testing Season Observed by SecurityHQ (Nov–Dec 2025)
As the year drew to a close, SecurityHQ’s global SOC entered one of its busiest periods. From November through December 2025, organizations across North America, EMEA, APAC, and LATAM scheduled year-end penetration testing and red team exercises to validate their security posture before the new fiscal year.
Early Reconnaissance: Mapping the Identity Landscape
In multiple customer environments, pentesters began quietly. Using LDAP queries, they enumerated Active Directory structures, probing for pre-authentication enabled accounts—a classic foothold for later abuse. SecurityHQ analysts noticed a surge in read-heavy directory queries, far exceeding normal user behavior baselines.
Soon after, the focus shifted to high-value groups. Enumerations of Domain Admins and Enterprise Admins were performed repeatedly, sometimes using native Windows tools, other times via popular AD enumeration frameworks. In mature environments, these queries triggered decoy account interactions, immediately flagging malicious intent.
Parallel to these activities, Pen testers conducted discovery scans, sweeping some known ports running windows services that can pave the way for lateral movement. In several cases, testers attempted DNS zone transfer requests, hoping to extract internal naming conventions and asset inventories.
Credential Access: Testing Human Weakness
The activity continued with password spray attacks. Pentesters tested commonly used passwords across large user populations, carefully staying below lockout thresholds.
SecurityHQ’s behavioral analytics detected the low-and-slow authentication failures and correlated them with earlier enumeration activity, forming a complete attack narrative.
Privilege Escalation Attempts: Ticket-Based Attacks
As reconnaissance matured, pentesters escalated to Kerberos abuse techniques.
SecurityHQ telemetry showed:
- Kerberoasting attempts, where service accounts with SPNs were targeted for offline password cracking.
- AS-REP Roasting, leveraging accounts with disabled pre-authentication to request encrypted authentication material.
These activities stood out due to abnormal Kerberos ticket request patterns.
| Logical Phase | Pentester Activity | SecurityHQ Use Case Coverage |
| Network Discovery | Discovery scans for open services/ports | ✔️ Covered |
| Network Discovery | Zone transfer request | ✔️ Covered |
| Directory Recon | AD/DC enumeration using LDAP queries | ✔️ Covered |
| Directory Recon | Excessive domain object queries | ✔️ Covered |
| Directory Recon | Default Admin Group Enumeration | ✔️ Covered |
| Target Identification | Identify pre-auth enabled accounts | ✔️ Covered |
| Target Identification | Decoy account enumeration | ✔️ Covered |
| Credential Access | AS-REP Roasting | ✔️ Covered |
| Credential Access | Kerberoasting | ✔️ Covered |
| Authentication Abuse | Password spray | ✔️ Covered |
LDAP AS-REP Roasting
Any of the AD account can be used suddenly to produce a burst of login events on the active directory. Mostly it is the the tool or a script that rapidly queries directory information, attempting to identify privileged roles, access paths, and high-value accounts. Credentials of the account are generally hard coded or embedded within the tool or script being used.
SecurityHQ’s Threat Detection team have developed logic that uses LDAP Active Directory Services event log file available under C:\Windows\System32\winevt\Logs
Rule Name: Authentication: Windows – Possible LDAP AS-REP Roasting
Detection Scope: Monitors LDAP and Kerberos authentication activity across Active Directory domain controllers.
Why it matters: Exposed Kerberos responses can be cracked offline, potentially leading to credential compromise without triggering repeated login failures. Early detection of this behavior helps identify credential access attempts before attackers escalate privileges or move laterally.
MITRE ATT&CK Mapping
TA0006 – Credential Access
T1558.004 – Steal or Forge Kerberos Tickets: AS-REP Roasting.
Threat Management
SecurityHQ’s Threat Management Team manages various endpoint security, cloud security and network security solutions for customers. Following section highlights some key security insights.
Alert: Multiple Suspicious Script and Reconnaissance Activities Detected (INC #1460383)
Detection: An incident was detected using Microsoft Defender for Endpoint (MDE) alerts and telmetries on December 8th, 2025, indicating multiple suspicious activities. The alert covered abnormal script execution, potential persistence mechanisms, defense evasion techniques, and domain reconnaissance activity originating from a single internal endpoint. The activity was classified as suspicious due to the combination of tools and techniques commonly associated with malicious actor behavior.
Investigation: On December 8th, 2025, Microsoft Defender for Endpoint detected a sequence of suspicious actions initiated from a remote interactive session originating from an internal source IP. The activity involved the use of built-in Windows utilities and scripting engines that are commonly abused by threat actors. Notably, the NLTest utility was executed with the /domain_trusts parameter to enumerate domain trust relationships, a behavior indicative of Active Directory reconnaissance and often observed during ransomware operations or lateral movement preparation.
Shortly thereafter, additional suspicious behavior was identified, including the abuse of Rundll32 to execute JavaScript, a known living-off-the-land technique used to evade security controls, and wscript execution modifying registry keys related to proxy configuration, which could enable interception or redirection of web traffic. PowerShell was also observed as part of the activity chain, with the associated file hash reviewed through threat intelligence sources. The combination of script-based execution, system enumeration, and potential proxy manipulation strongly suggests intentional reconnaissance and defense evasion, rather than legitimate administrative activity.
Response Action taken:
- SOC Raised Major Incident and informed customer over call.
- Threat Management Team blocked identified IOCs and updated the incident.
- The malicious process was successfully blocked and terminated by Microsoft Defender.
- No further suspicious activity has been observed. Full antivirus scan has been performed across the entire host to ensure no residual malware components remain active
Alert: MDE: Pass the Hash followed by brute force was detected on Windows server. (INC #1471047)
Detection: An incident was detected using Microsoft Defender for Endpoint (MDE) alerts and telmetries on December 16th, 2025,, indicating suspicious lateral movement activity and remote command execution on device. The alert identified ‘SuspRemoteCmdCommand’ malware associated with WMI process execution originating from an external IP address.
Investigation: On December 16th, 2025, security monitoring identified a successful network logon (Event ID 4624) using an anonymous authentication context over NTLM, originating from an internal source IP and targeting domain controller infrastructure. The authentication leveraged NTLM V1 with a key length of zero via the NtLmSsp logon process, which is highly anomalous and consistent with Pass-the-Hash–style activity. During the same timeframe, multiple indicators of credential abuse were observed, including failed NTLM authentication attempts for privileged accounts, enumeration of a large number of user accounts consistent with a dictionary-style attack, and repeated access attempts to administrative and IPC shares. Additional LDAP query activity against directory services further suggested reconnaissance behavior focused on domain discovery.
Subsequent investigation revealed a broader pattern of post-authentication activity, including the creation of new processes associated with agent-style executables, the addition of multiple network share objects, and repeated access to SYSVOL, NETLOGON, and IPC$ shares from the same source. Follow-on actions included the creation and password reset of new computer accounts within the domain, successful network logons tied to the same source IP, and directory read access across multiple domain controller shares, all indicative of lateral movement and persistence preparation. In parallel, sensitive recovery material was accessed via directory and cloud interfaces, increasing the overall risk severity. Taken together, the activity strongly aligns with credential misuse, lateral movement, and domain-level reconnaissance, rather than legitimate administrative operations.
Response Action taken:
- SOC Raised Major Incident and informed customer over call.
- Threat Management Team blocked identified IOCs and updated the incident.
- Running Malicious processes were terminated, Residues cleared by the Threat Management analyst.
- No further suspicious activity has been observed. Full antivirus scan has been performed across the entire host to ensure no residual malware components remain active.
Threat Hunting
SecurityHQ’ s Threat Hunting team conducted hunts focused in general email activities seen in the customer’s environment. Following section highlights some of the key findings and recommendations that were communicated to affected customers.
Context: Suspicious and abnormal email communication patterns were observed across the organizations, indicating a potential risk of data exfiltration, unauthorized information disclosure, or insider misuse. These behaviors include frequent communication with competitor domains, outbound emails sent outside business hours, attachments sent to free or personal email services, and anomalous email activity linked to departing employee accounts.
The objective of these hypotheses was to proactively detect, investigate, and respond to email-based data leakage risks, ensuring sensitive business information is not transferred outside the enterprise without authorization and strengthening the overall email security posture.
Notable Observations: Across the environment, the threat hunt identified multiple high-risk email behaviors. Key findings are summarized below:
Extensive Communication with Competitor Domains
A significant volume of email communication was observed between internal users and competitor domains. List of competitor domains were shared proactively by few organisations with matured security program.
Key Observations:
- On an average 1-2 percent of total emails were identified involving competitor domains.
- Top competitor domains included key competitors for the company.
- Repeated high-frequency communications from a small subset of users. Subject lines referenced agreements, contracts, approvals, financial statements, tax and legal matters, increasing data sensitivity concerns.
Associated Risk: These patterns may indicate unauthorized sharing of confidential business information, competitive intelligence leakage, or misuse of corporate email channels. This highlights importance of adding competitor domains on watchlist to detect unapproved/intentional data leakage.
Out-of-Business Hours External Email Activity
Outbound emails sent between 7 PM and 7 AM showed elevated volumes toward external recipients.
Key Observations:
- Multiple users sent hundreds of emails to external recipients during non-business hours.
- Several emails were linked to payment-related or financial subjects.
- Activity occurred during low-visibility periods, reducing detection likelihood.
Associated Risks: Email activity during off-hours increases the risk of covert data exfiltration, especially when financial or sensitive business information is involved.
Email Activity from Departing / Disabled Accounts
Email activity was analyzed for users whose accounts were disabled in the last 30 days.
Key Observations:
- No clear evidence of malicious behavior immediately prior to account disablement were observed by SecurityHQ Team.
- From past experiences, Typically leavers tend to forward document as an email attachment to their personal email accounts.
- Associated Risk: Although not conclusively malicious, data leakage risk increases during employee offboarding, especially when legal or financial documents are involved.
Emails Sent to Free & Personal External Email Domains
Significant email traffic was observed toward free external email providers in organization where these domains are not explicitly blocked.
Key Observations:
- On average, 10 percent of total email trails involving free external domains.
- 70 percent of total emails sent, appeared to be sent to potential personal email accounts.
- All flagged emails included attachments.
Associated Risk: Sending attachments to personal email accounts is a well-known insider threat and data exfiltration technique, presenting one of the highest leakage risks identified in this hunt.
External Email Auto-Forwarding Indicators
While external auto-forwarding appears largely restricted, related behaviors were still noted.
Key Observations:
- No widespread misconfiguration allowing automatic forwarding was identified.
- Users were observed manually forwarding emails to external accounts.
- Lack of user awareness regarding the risks of external forwarding.
Associated Risk: Manual forwarding can bypass technical controls and enables silent, persistent data exfiltration if not properly monitored.
Hypothesis Status:
- The threat hunt identified multiple email communication behaviors that increase the risk of data exfiltration, although no confirmed malicious breach was detected.
- High-volume communication with competitor domains, combined with sensitive subject lines, represents a moderate to high data leakage risk.
- Out-of-business-hours emailing and attachment sharing to free or personal domains significantly elevates insider threat exposure.
- Departing employee accounts did not show over malicious intent but still warrant validation due to the nature of shared content.
- Overall, the findings highlight control gaps, monitoring blind spots, and awareness issues that could be exploited for unauthorized data disclosure if left unaddressed.
Recommendations: Based on the observed email threat landscape, the following actions are recommended
- Enforce DLP policies to detect and block sensitive financial, legal, and confidential content in outbound emails.
- Block or quarantine attachments sent to free and personal external email domains.
- Enable automatic encryption and mandatory classification for sensitive outbound email attachments.
- Monitor and alert on outbound emails sent to external recipients outside business hours.
- Trigger alerts when users send an unusually high number of attachments to new external recipients.
- Continuously monitor and review communications with competitor domains.
- Perform enhanced email activity reviews for users during employee offboarding periods.
- Restrict external email capabilities for departing users where business-justified.
- Educate users on risks associated with forwarding corporate emails to personal accounts.
- Periodically audit external email forwarding behaviors and policy exceptions.
Incident Response Success Story
Incident Story: X (Formerly Known as Twitter) Account Compromised Linked to corporate domain
SecurityHQ’s Incident Response (IR) team was engaged following a suspected account takeover involving Apple IDs, social media accounts, and mobile devices. The attack leveraged leaked personal data, phishing, and session hijacking techniques to bypass MFA and gain persistent access.
The incident began when an attacker obtained leaked personal data from an external breach. Using this information, the attacker crafted a highly targeted phishing email impersonating Apple security communications.
The phishing email prompted the victim to consent to Apple account access, unknowingly authorizing a malicious OAuth session. This allowed the attacker to bypass MFA via session hijacking.
With valid session access, the attacker logged in using the leaked credentials and began account persistence actions:
- Recovery email was changed on the X (Twitter) account
- Mobile number was updated on Telegram
- Deleted old tweets.
Investigation revealed that a single Session ID was accessed from multiple geographically disparate locations simultaneously. This anomaly provides definitive evidence of Session Hijacking, indicating that the attacker stole the valid session token and replayed it from a remote infrastructure to bypass Multi-Factor Authentication(MFA).
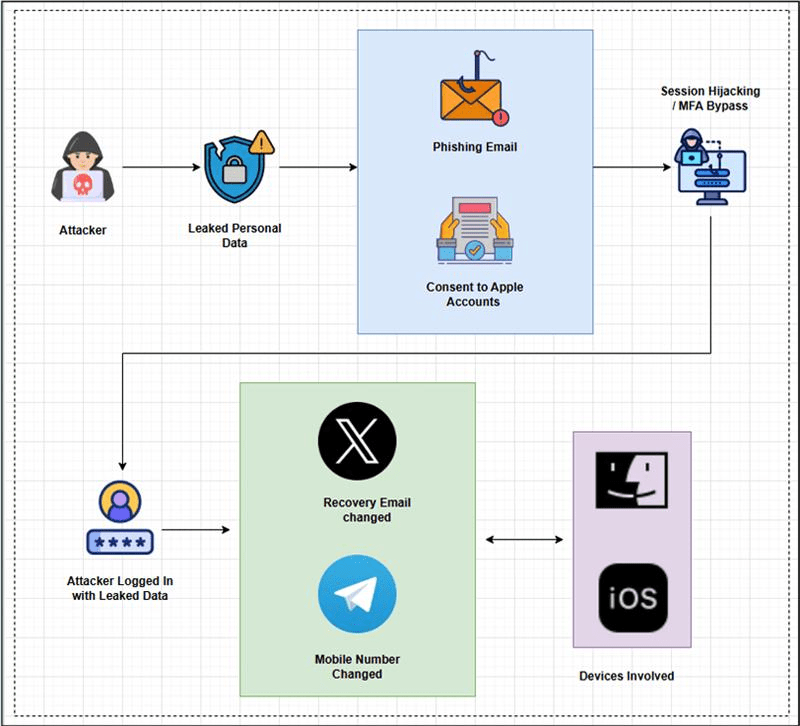
The user’s personal Apple ID appeared in multiple breach datasets, and both personal and corporate accounts were active on the same device. This strongly supports a session hijacking pathway originating from the compromised personal account, enabling access to the corporate session without requiring the corporate password.
No direct evidence of corporate credential leakage was found on the dark web, and no further lateral movement was identified.
SecurityHQ Incident Response team shared tactical and strategical recommendation to prevent recurrence of similar incidents in future.
Authors:




![10 Tips to Protect Your Data [Infographic]](https://www.securityhq.com/wp-content/uploads/2021/07/Thumbnail-image-Tips-to-Protect-Your-Data-blog-copy.jpg)