Visibility and Control For Every Risk
attack surface to reduce risk and strengthen resilience.
Why SecurityHQ?
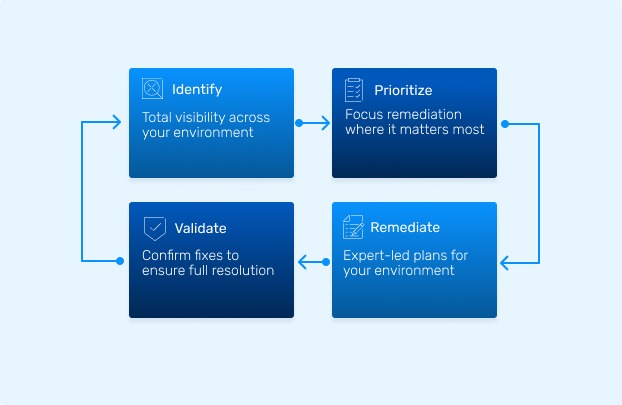
Our analysts validate and prioritize risk using dynamic scoring models that factor in exploitability, asset exposure, and attacker behavior.
We provide targeted remediation support based on real-world attacker behavior informed by threat intelligence and TTP mapping.
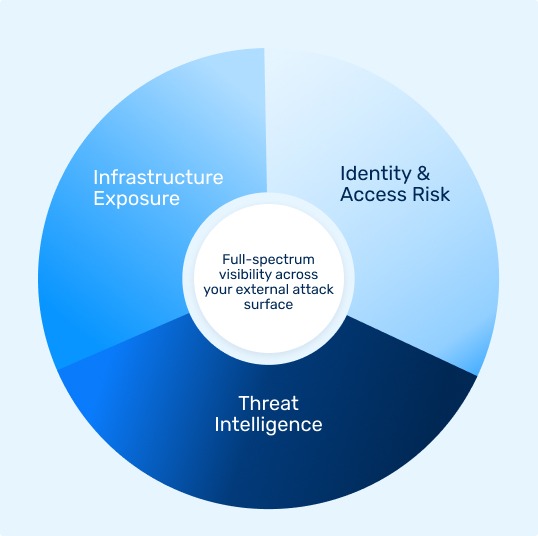
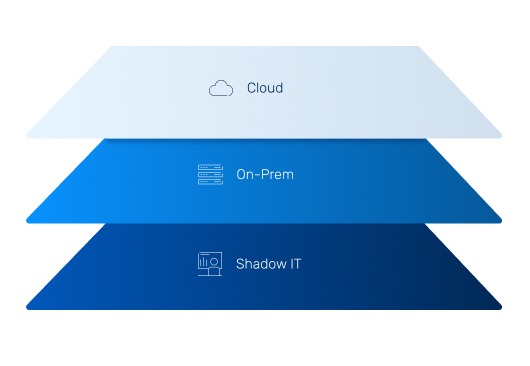
Our team track exposures across cloud, on-prem, web apps, OT, containers, and identity systems —not just your endpoints.
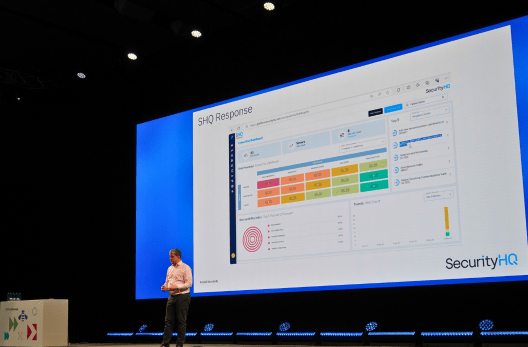
The SHQ platfom consolidates asset, identity, and vulnerability data for continuous monitoring and context-rich reporting.
Expertise to Keep You Ahead of Threats
Powered by Real-World Intelligence
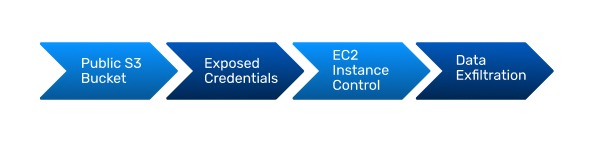
Precise Remediation
No Blind Spots
Add-Ons for Focused Risk Areas
Take Control Of Your Attack Surface
What You Can Expect
A standing forum to review active exposures with your consultant, resolve blockers, and keep remediation efforts moving.
All vulnerability data is consolidated into a single view, supported by analyst-led validation to focus your attention where it’s needed most.
Need 24/7/365 Vulnerability Exposure Management
for your organization?
"*" indicates required fields